Privileged accounts are keys to critical systems and data. These keys can be dangerous if misused. The just-in-time (JIT) approach to privileged access management (PAM) solves this issue by aligning access, user needs, and time.
In this post, we explain what just-in-time privileged access management is and how it helps organizations enhance their cybersecurity. Security officers in particular, and anyone else interested in efficient ways of controlling privileged access, will find valuable insights within.
Key takeaways:
- The traditional PAM approaches do not eliminate standing privileges, which pose security risks and extend the attack surface.
- With JIT PAM, users are granted only the access they need, for a limited time, and for a valid reason.
- To successfully adopt JIT privileged account management, create clear policies, leverage account discovery, limit privileges to the bare minimum, and deploy specialized PAM solutions.
- With a cybersecurity platform like Syteca, organizations can implement just-in-time security with granular access controls, approval workflows, session monitoring, and incident response.
What is the just-in-time approach to privileged access management?
Just-in-time privileged access management (JIT PAM) ensures that only the right users are provided with privileged access to specific systems and resources, only for a valid reason, and only for the time required. The JIT PAM model helps organizations implement the cybersecurity principle of least privilege, with zero standing privileges as the goal.
The idea behind JIT PAM is to grant access permissions only when users need to perform a certain task and for no longer than the time required to fulfill that task. This minimizes the risk of privileged users taking advantage of sensitive data or privileged accounts being abused by attackers.
How JIT PAM works
Instead of keeping permanent privileged rights, user accounts receive time-bound permissions that automatically expire once the task is done.

To help you understand the JIT PAM access workflow, let’s take a look at its key stages:
- Access request: A user requests privileged access to a system or resource, specifying the reason or task for which it’s needed.
- Policy check: The system verifies if access is allowed based on user role, time, identity verification, or other contextual factors.
- Admin approval: The manager, sysadmin, or security team manually approves the access request.
- Time-limited access provisioning: The system grants temporary permissions based on the user’s request.
- Session monitoring: User activity is monitored and recorded for security and compliance purposes.
- Access revocation: Once the task is completed or the time expires, access is revoked, leaving no standing privileges.
This is an example of a classic approval-based JIT PAM workflow, where employees verify access manually. Some JIT PAM systems skip the manual approval step, automatically granting access based on policies and contextual details.
Why choose JIT PAM over the basic PAM approach?
Many organizations still follow only basic PAM practices that mostly focus on securing existing privileged accounts and managing privileged passwords. However, the evolving role of privileged access management in business today demands more comprehensive strategies to effectively mitigate insider threats, meet compliance needs, and ensure operational agility.
The biggest mistakes companies make by implementing basic PAM practices are:
- Granting too many access rights to privileged users
- Providing users with standing privileges
- Granting unnecessary privileges
- Creating personal privileged accounts for privileged users
While a basic PAM method helps businesses meet compliance requirements and make sure that employees and third parties use their privileges in an authorized manner, it’s not enough to meet the principle of least privilege.
The risk of users with excessive as well as standing privileges remains high, even with PAM tools in place. Identity and access management leaders must implement just enough privilege and just-in-time strategies to minimize the risk of standing privileges.
Gartner, “Reduce Risk Through a Just-in-Time Approach to PAM”, 11 April 2025 (Gartner subscription required)
The cornerstone of the JIT PAM principle is to provide users with only the access they need for the time they need it and then to remove that access or privilege. On the contrary, most organizations tend to provide privileged users with access to sensitive information on a permanent basis.
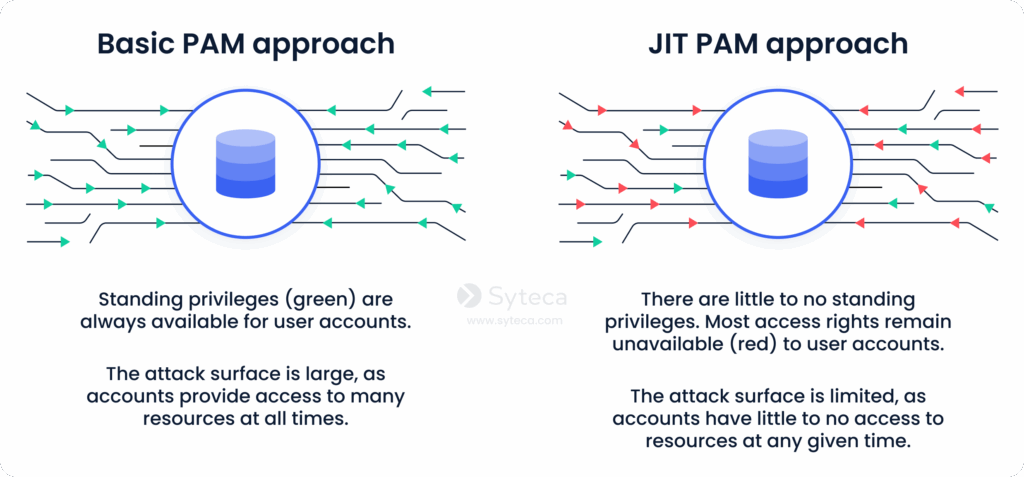
To implement the principle of least privilege to the fullest extent, you need to apply the zero standing privileges strategy through a JIT PAM model. This includes eliminating standing or always-on privileges to reduce your attack surface.
Request access to Syteca’s online demo!
Learn how Syteca can help you implement JIT PAM and secure access to endpoints.
The benefits of just-in-time access
Even with PAM in place, standing privileges can compromise your organization’s sensitive systems and data. Your critical assets can be compromised in multiple ways:
- An employee or a third party may misuse their privileges and provide sensitive data to your competitors.
- Users may break cybersecurity policies and make inadvertent mistakes that put your assets at risk.
- Malicious actors may steal credentials to your privileged accounts and gain access to your confidential information.
- Former employees or contractors might utilize their old accounts for revenge.
- An abandoned privileged account (for instance, the account of an ex-employee) is more likely to be hacked than an actively managed account.
Let’s now explore five major benefits of the just-in-time PAM approach and see which risks it can eliminate.
1. Least privilege in action
The principle of least privilege requires organizations to remove unnecessary access rights and provide them only if absolutely necessary. All privileges for all users should be limited to the bare minimum needed to perform their work.
2. Reduced insider risk
Employees, contractors, or other insiders with constant access to your systems pose a higher risk, whether intentional or accidental. By making privileged access temporary and auditable, JIT PAM makes it much harder to misuse access rights without being detected.
3. Streamlined compliance and auditability
Cybersecurity frameworks like NIS2, DORA, and NIST 800-171 require strict access control over privileged access. With detailed logs of every access attempt and action performed under privileged accounts, JIT PAM ensures compliance with cybersecurity requirements and increases accountability.
4. Fewer accounts
To adopt an advanced JIT PAM approach, organizations may choose not to create privileged accounts at all. Instead, time-limited privileges can be requested. Access is granted only if a request meets the required parameters. In this way, organizations minimize the risks of account misuse, reduce the number of inadvertent mistakes made by privileged users, and eliminate the need for managing privileged accounts altogether.
5. Faster access to resources
The need to constantly manage permanent accounts can slow down your workflows and processes. Modern JIT PAM solutions can streamline access provisioning by automatically approving access requests based on defined policies or contextual factors. Thus, users can quickly access what they need without compromising security.
What to consider when adopting JIT PAM
To protect your critical assets from malicious insiders and unintended harm, JIT PAM has to be implemented thoughtfully and efficiently. This includes integrating dedicated privileged access management solutions to prevent unauthorized activities.
How to adopt the JIT PAM approach
1
Identify systems and data to be secured
2
Create a JIT PAM policy
3
Select JIT PAM techniques
4
Minimize activity to what’s necessary
5
Implement multi-factor authentication
6
Leverage account discovery
7
Choose a customizable PAM tool
1. Identify systems and data to be secured
Map out your most critical organizational assets: data, servers, applications, and databases. This step will help you prioritize what to protect first and apply JIT PAM where it matters most. Then define which users can request specific privileges for work purposes and which can perform all their tasks without requesting additional access.
2. Create a JIT PAM policy
A JIT PAM policy defines who can request privileged access, when, and how. A well-written policy also outlines the conditions for access time restrictions, approval workflows, monitoring requirements, and conditions for creating and deleting accounts, among other considerations. With such a policy, you can ensure consistency and compliance when enforcing just-in-time access.
3. Select JIT PAM techniques
The next stage is identifying the right techniques to efficiently implement JIT PAM in your organization. There are several different methods, including temporary role assignments, time-bound secret provisioning, and ephemeral accounts (temporary on-demand user accounts that are deleted automatically after the session ends). The JIT PAM techniques you use will largely depend on your organization’s IT infrastructure and the access management solution of your choice. Don’t forget to balance security with usability, as well-designed JIT PAM must not generate friction or resistance from your staff.
4. Minimize activities to what’s necessary
Even with time-limited access, a malicious insider or an external attacker can manage to compromise sensitive data. Consider restricting privileged sessions and the scope of actions to the bare minimum. Thus, you’ll limit the potential for misuse or mistakes by users with elevated access, enforcing the principle of least privilege at a very granular level.
5. Implement multi-factor authentication
To further prevent the risk of unauthorized access, implement multi-factor authentication. Two or more authentication factors help you verify user identities, so you know your users are who they claim to be.
6. Leverage account discovery
Account discovery in PAM is a critical feature that enables you to identify the default, unmanaged, and forgotten human and service accounts that pose a constant risk. By detecting such accounts, you can take control of them and eliminate any potential backdoors for malicious actors to exploit.
7. Choose a customizable PAM tool
Search for flexible privileged access management solutions that offer customizable options, so you won’t have to pay for features you don’t use. In addition, consider the solution’s integration capabilities and the ability to customize access workflows. A good PAM solution also provides privileged user monitoring, incident response, and reporting to support compliance.
And remember, in the long term, JIT PAM initiatives can save you more money than they cost.
Adopting a JIT PAM approach requires sophisticated software with features to monitor and record privileged user activity, provide access to critical data after approval, detect abnormal activity, and respond to it immediately.
How can Syteca help you implement a JIT PAM approach?
Syteca is a comprehensive cybersecurity platform that enables organizations to protect their internal IT environments. Syteca PAM offers a wide range of features to help you implement privileged access management best practices, monitor user activity, and respond to incidents.
Syteca can help you implement the just-in-time approach to PAM as follows:
Implement JIT PAM with Syteca
Leverage Syteca PAM to granularly provide and revoke access to critical servers and workstations
Provide employees and third-party vendors with one-time passwords and time-limited sessions to minimize the exposure of assets
Provide users with JIT privileged access to the most critical endpoints only after manual approval
Integrate with ticketing systems
Apply the principle of purpose-based access to high-risk sessions by requiring users to provide ticket numbers
Detect unmanaged accounts
Eliminate security blind spots by discovering and onboarding orphaned privileged accounts in your infrastructure
Monitor privileged activity
Track every action of privileged users and record sessions for enhanced accountability and potential investigations
With robust PAM, UAM, and incident response, the Syteca platform enables you to adopt a holistic approach to cybersecurity and prevent insider threat incidents.
Eliminate standing privileges with JIT PAM
Leveraging the just-in-time approach to privileged access management is a sure-fire way to take your cybersecurity to the next level. By providing privileged users with the access they require for only the time needed to complete their tasks, you minimize the chances of data being stolen or compromised.
The most important thing to remember is that zero standing privileges and just-in-time access control approaches also require the use of other security techniques like privileged user monitoring, session recording, and secure authentication. Syteca offers an advanced solution for managing privileged access, including major features to implement JIT PAM.
Want to try Syteca? Request access
to the online demo!
See why clients from 70+ countries already use Syteca.