From AI-powered attacks to supply chain breaches, the cybersecurity threats are growing in speed, scale, and sophistication. This article gives you 12 essential cybersecurity practices to build resilience, reduce risk, and protect your organization’s most valuable assets in 2026 and beyond.
Key takeaways:
- With global cybercrime costs expected to reach $12.2 trillion annually by 2031, cybersecurity for businesses is critical.
- Cloud security, zero trust, AI-driven threats and security defenses, supply chain risk, and strict compliance regulations shape modern cybersecurity.
- Robust cybersecurity policies, people-centric security, access controls, password management, and supply chain risk management can help your business mitigate cybersecurity risks.
- Streamline enterprise cybersecurity defenses with cybersecurity solutions that provide privileged access management (PAM) and identity threat detection and response (ITDR) capabilities.
Why is cybersecurity important for your organization?
Today, organizations heavily rely on technology and generally store their sensitive data in digital formats, making it a prime target for cybercriminals. From intellectual property to PII, sensitive data attracts cybercriminals for financial gain, espionage, and other reasons. As we can see from real-life examples of cybersecurity breaches, the consequences of cyberattacks may be devastating, ranging from reputational damage to business disruptions.
However, implementing robust network security best practices and measures described below can help you build a secure IT environment.
Benefits of implementing best practices in cybersecurity
Here are the key benefits of implementing cybersecurity tips and best practices:
Top 6 benefits of improving organizational security
1. Protect sensitive data
Strong and relevant cybersecurity controls help your organization prevent data breaches that could expose sensitive data, including client information, trade secrets, and marketing strategies.
2. Prevent financial losses
Effective cybersecurity measures significantly reduce the financial impact of cyberattacks, including ransomware payments, legal penalties, operational downtime, and remediation costs.
3. Maintain business continuity
Robust cybersecurity can protect your organization from breaches that cause downtime and disruption. If an incident does occur, having the proper protections, backups, and response plans minimizes these risks.
By publicly demonstrating your commitment to safeguarding information, your organization can earn customer trust and loyalty. In turn, you’ll gain a competitive advantage based on consumer confidence.
5. Reduce cybersecurity insurance premiums
Stronger security controls mean lower risk, which brings more trust from cyber insurers. This often translates into more favorable policy terms and lower premiums.
6. Comply with cybersecurity regulations
Implementing the required defense mechanisms helps your organization meet the legal obligations and cybersecurity recommendations of NIS2, the GDPR, and industry-specific standards, thus avoiding costly fines. Compliance also enhances transparency and accountability across your organization.
To bring you up to date on the current cybersecurity landscape, let us first guide you through the main focus points for 2026.
What should your cybersecurity focus on in 2026?
Cybersecurity Ventures, a leading global research and market intelligence firm, predicts [PDF] the annual global cost of damage due to cybercrime will reach $12.2 trillion by 2031.
Organizations will continue spending more on cybersecurity to manage the risks of an expanding attack surface, which is largely caused by the following factors:

- Remote work. Remote work remains the default for many organizations, creating a lack of visibility and control over employees. Remote environments are harder to secure, as they lie outside organizations’ perimeters. Hybrid work environments are also a source of risk, as they expand the area of potential attacks. When cybersecurity officers must protect both in-house and remote environments, it increases the possibility of human error and, eventually, a breach.
- Cloud infrastructure complexity. Gartner predicts that organizations’ spending on public cloud services will exceed $1 trillion through 2027, which will comprise approximately18% of total IT spending. Securing cloud infrastructure may be challenging due to the complexity of cloud environments and the sharing of security responsibilities between the client and the cloud service provider. Additionally, it’s challenging to maintain consistent security policies across cloud and hybrid environments, which creates opportunities for attackers to exploit misconfigurations and overprivileged roles.
- Expansion of AI systems and agents. Organizations are rapidly deploying AI-enabled applications and APIs, which frequently do not get monitored. Another particularly novel risk is the use of autonomous AI agents and systems that communicate with each other without cryptographic verification and proper protection.
- Supply chain dependencies. The supply chain remains a common point of cybersecurity failures. As the number of third parties you interact with grows, so does the potential for hackers to access your infrastructure. Beyond your direct suppliers, there are fourth- and fifth-party dependencies that lie outside your visibility and control.
- Convergence of IT, OT, and IoT. Security measures and protocols for the Internet of Things (IoT) and operational technology (OT) are still developing, exposing their connected IT systems to cybersecurity risks. Cyber attackers may use IoT and OT devices as entry points to your core IT infrastructure.
- Proliferation of APIs and shadow endpoints. According to Gartner’s 2025 Market Guide for API Protection, “API attacks are a major concern for security leaders”. With 99% of organizations experiencing API security issues, the challenge is real. Many organizations remain unaware of all the APIs their development teams have created. On top of that, shadow or forgotten endpoints, which are rarely documented or properly secured, increase the risk of attacks.
- AI-driven attacks. AI attacks can now operate with unprecedented automation and adaptability. Unlike human-led attacks that adjust tactics over hours, autonomous AI systems and malicious code can evolve in seconds, learning from failed attempts, replicating successful ones, and scaling their attacks.
By 2027, AI agents will reduce the time it takes to exploit account exposures by 50%… AI agents will enable automation for more steps in ATO [account takeover], from social engineering based on deepfake voices, to end-to-end automation of user credential abuses. Because of this, vendors will introduce products web, app, API and voice channels to detect, monitor and classify interactions involving AI agents.
Jeremy D’Hoinne, VP Analyst at Gartner
When securing your organization’s infrastructure for 2026, focus on the following cybersecurity trends:
8 cybersecurity trends to consider in 2026
Developing cloud security
Mastering digital provenance
Implementing zero trust at scale
Enhancing identity security
Implementing preemptive cybersecurity
Augmenting supply chain infrastructure
Complying with stricter cybersecurity requirements
Developing cloud security
The rapid rate of cloud migration in recent years hasn’t left time for cybersecurity to catch up. Poorly secured remote work environments from which cloud services are often accessed, the complexity of hybrid cloud infrastructures, and other cloud vulnerabilities are pushing the cloud security industry to develop quickly.
Embracing AI development
The development of artificial intelligence (AI) technology raises a series of concerns in cybersecurity. Hackers leverage cutting-edge technologies like AI, machine learning, and automation to orchestrate highly sophisticated attacks. Generative and third-party AI tools also pose data confidentiality risks, according to Gartner. In 2026, organizations will focus on adapting their cybersecurity strategies and using robust machine learning technologies in their favor.
The rapid growth of generative AI (GenAI) is expanding the threat landscape. At the same time, the evolving regulatory landscape and the alarming frequency of cyberattacks are prompting SRM leaders to increase their spending on security measures. Organizations are also strategically improving their defenses by adopting advanced technologies and security solutions which enable them to proactively identify potential vulnerabilities or malicious activities across various digital platforms.
Shailendra Upadhyay, Senior Research Principal at Gartner
Mastering digital provenance
As organizations increasingly use third-party software and AI-generated content, verifying the source and authenticity of data and software is critical. This is known as digital provenance. In the foreseeable future, companies that fail to carry out digital provenance could face compliance fines and sanctions, potentially costing billions.
Implementing zero trust at scale
According to Gartner (subscription required), adoption of zero trust programs is going to accelerate in the coming years. It is worth mentioning, though, that zero trust must be combined with broader cybersecurity strategies, as cyberattackers will continue targeting vulnerabilities outside zero trust architectural scope, particularly through APIs, social engineering, and supply chain vectors.
Gartner states that data privacy concerns related to the development of AI will boost the establishment of new security regulations. According to another post by Gartner, “75% of the global population will have its personal data covered under privacy regulations in 2024,” up from 10% in 2020. Following updates to cybersecurity laws, standards, and regulations is crucial for staying compliant and protecting your organization’s data.
Enhancing identity security
Organizations are increasingly recognizing that identity is the new critical perimeter to secure in distributed, hybrid, and multi-cloud environments. With the identity perimeter becoming the primary attack surface, identity threat detection and response (ITDR) represents a fundamental shift in security that will continue into 2026 and beyond. By 2029, the global ITDR market is expected to reach approximately $35.6 billion from just $12.8 billion in 2024, with a projected annual growth rate of 22.6%.
Implementing preemptive cybersecurity
According to Gartner’s ebook on the top 2026 strategic technology trends, the cybersecurity industry is shifting focus from reactive “detect and respond” approaches to proactive “predict and prevent” ones. Gartner says this approach will use AI-powered analytics, deception, and automation to anticipate and neutralize threats before they occur.
Augmenting supply chain infrastructure
In 2026, cybersecurity specialists are expected to pursue new ways to protect supply chains and develop existing methods of cybersecurity supply chain risk management. This is primarily a response to cases of espionage, state-driven cyberattacks, and geopolitical disturbances that affect the global supply chain.
Complying with stricter cybersecurity requirements
Governments worldwide are advancing their efforts to secure their citizens’ personal data, pushing financial institutions to adopt advanced cybersecurity solutions for banks and align with complex regulations like PCI DSS. At the same time, industries such as healthcare, manufacturing, and critical infrastructure are also ramping up their cybersecurity investments to meet the compliance demands of NIS2, DORA, and other regulations.
Explore the power of Syteca now!
Test how Syteca can deter, detect, and disrupt insider threats in your IT infrastructure now!
Continue reading for a list of what you can do in 2026 to protect your organization against cyber attacks.
Top 12 cybersecurity best practices for 2026
Here, you’ll find our checklist of new and time-tested cybersecurity recommendations to help your organization prevent cyber attacks in 2026:

1. Establish a robust cybersecurity policy
A cybersecurity policy serves as a formal guide to all measures used in your company to improve cybersecurity efficiency. This policy ensures your security specialists and employees are on the same page and describes essential and company-wide information security practices.
Consider implementing a hierarchical cybersecurity policy that consists of a single centralized policy and additional policies uniquely designed for each department within your organization. A hierarchical cybersecurity policy takes into account each department’s unique needs, helping you increase overall cybersecurity effectiveness and avoid workflow disruptions.
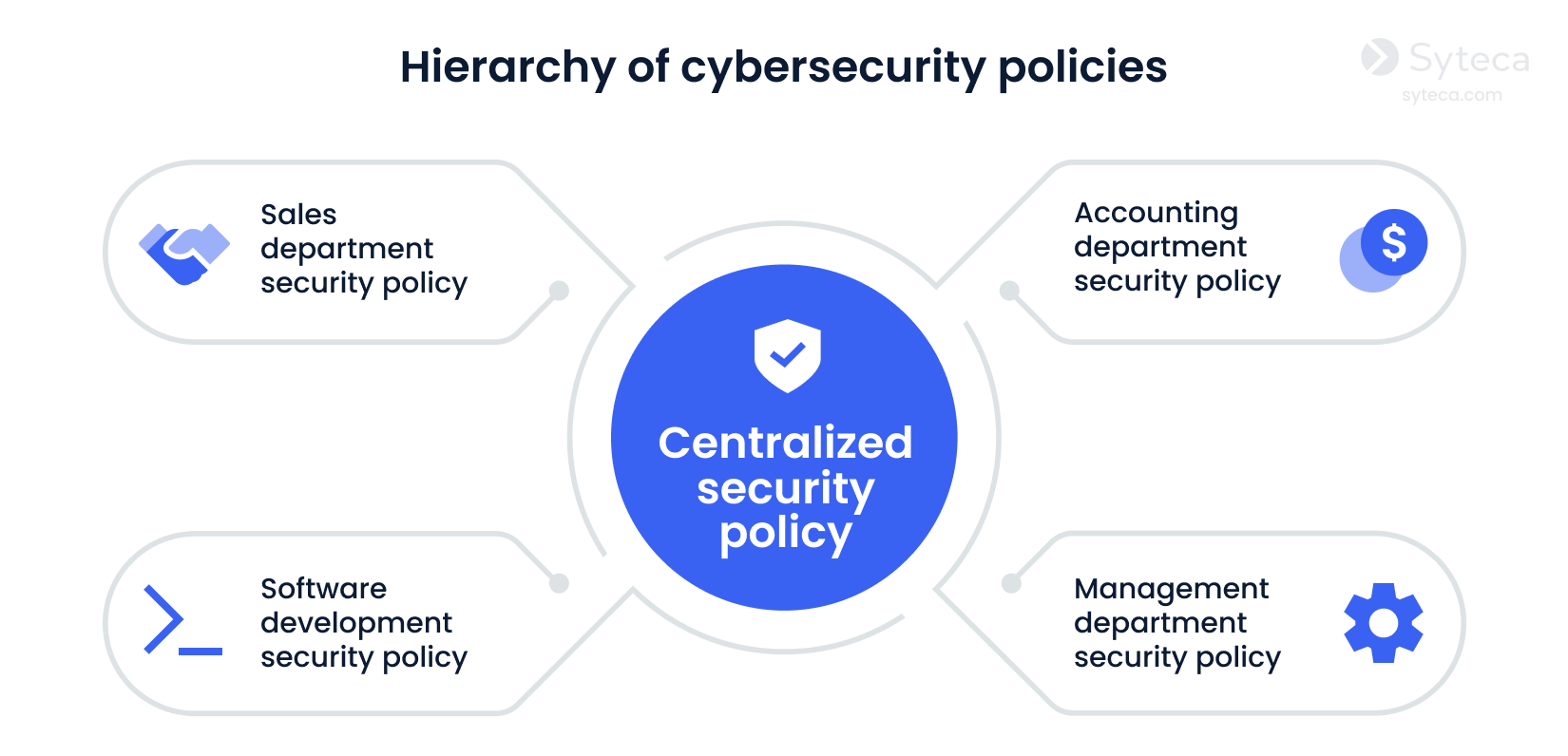
Similarly, you can design your security policies to address different issues or systems within your organization’s overall cybersecurity program. Among a wide variety of information security policy examples, we highly recommend developing an access control policy, a remote access policy, and a vendor management policy, for starters.
2. Secure your perimeter and IoT connections
Modern organizations’ perimeters extend far beyond firewalls and DMZs, as remote work, cloud environments, and IoT devices significantly extend the attack surface. IoT is a rising trend — the IoT market is expected to grow to $1,148 billion in 2030 from $959 billion in 2025, at a CAGR of 3.7%.
Security cameras, doorbells, smart door locks, heating systems, and office equipment — many of these are connected to the internet and can be used as potential attack vectors. A compromised printer, for instance, can allow malicious actors to view all printed or scanned documents.
Secure your perimeter by protecting your border routers and establishing screened subnets. To enhance enterprise database security, you can also separate sensitive data from your corporate network and limit access to such data.
Combine conventional protection measures like firewalls and VPNs with the zero trust model to protect yourself further. Based on the concept never trust, always verify, zero trust requires users and devices in your organization to be continually validated to prevent unauthorized access to users’ personal data.
3. Employ a people-centric security approach
A technology-centric approach to cybersecurity isn’t enough to ensure all-around protection, since hackers often use people as entry points. According to Verizon’s 2025 Data Breach Investigations Report, 60% of breaches involve a human element.
A people-centric approach can help you reduce human-related risks. In people-centric security, an important perimeter is the workers themselves. Educating and monitoring employees are the main elements of a secure, people-centric environment.
To make your organization’s cybersecurity people-centric, implement the following measures:

4. Control access to sensitive data
Granting employees many privileges by default allows them to access sensitive data even if they don’t need to. This approach increases the risk of insider threats and allows hackers to access sensitive data as soon as they compromise an employee’s account.
Applying the least permissions principle (also called the principle of least privilege) is a much better solution. It means assigning each user the fewest access rights possible and elevating privileges only when necessary. If access to sensitive data is not needed, corresponding privileges should be revoked.
In addition to the principle of least privilege and the zero trust model, a just-in-time approach to access management brings even more granularity to controlling user privileges. This approach means providing employees access by request for a specific time and a valid reason.
Your organization can also combine these access management techniques.

Pay special attention to who has remote access to your infrastructure. Securing your remote workforce requires a combination of measures, such as improving visibility into remote employees’ actions and properly configuring your networks. Learn how to avoid common mistakes in securing remote access to your organization in our article on the top 10 mistakes of security officers in protecting remote workplaces.
Privileged Access Management with Syteca
5. Manage passwords wisely
Employee credentials give cybercriminals direct access to your sensitive data and valuable business information. Brute force attacks, social engineering, and other methods can be used to compromise your employees’ credentials without their knowledge.
Organizations often implement best practices for password attack prevention by using specialized password management tools. These solutions give you control over your employees’ credentials, reducing the risk of account compromise.
Give preference to password management tools that provide passwordless authentication, one-time passwords, and password encryption capabilities.
For employees, add the following recommendations to your cybersecurity policy:
- Use a different password for each account
- Have separate accounts for personal and business use
- Use password managers and generators
- Use autofill on a trusted device to enter credentials
- Never share credentials with other employees
6. Use multi-factor authentication
Multi-factor authentication helps you protect sensitive data by adding an extra layer of security. With MFA activated, malicious actors cannot log in even if they possess your password. They would still need other authentication factors, such as your mobile phone, fingerprint, voice, or a security token.

While seemingly basic, MFA is among the best cybersecurity protection methods and is mandated by most cybersecurity standards, including the GDPR, PCI DSS, NIS2, and SWIFT CSP.
As an added benefit, MFA allows you to distinguish among users of shared accounts, improving your access control capabilities.
7. Monitor the activity of privileged and third-party users
Privileged users and third parties with access to your infrastructure have all the means to steal your sensitive data and remain undetected. Even if these users don’t act maliciously, they can unintentionally cause cybersecurity breaches.
To reduce the risks posed by privileged users and third parties, implement the following measures:

The most useful way to protect your sensitive data is by monitoring the activity of privileged and third-party users in your organization’s IT environment. User activity monitoring (UAM) can help you increase visibility, detect malicious activity, and collect evidence for forensic investigations.
Cybersecurity solutions with monitoring capabilities provide useful insights into who does what in your organization. Such tools track users’ actions in the form of screenshots and information such as visited websites, typed keystrokes, and opened applications.
Explore Syteca in action.
See how you can leverage Syteca’s user activity monitoring capabilities now!
8. Manage supply chain risks
Your vendors, partners, subcontractors, suppliers, and other third parties with access to your organization’s resources may be susceptible to supply chain attacks.
In a supply chain attack, cybercriminals can infiltrate or disrupt one of your suppliers and use that access to escalate the attack further down the supply chain, potentially affecting your organization. In the Snowflake data breaches, attackers gained unauthorised access to Snowflake accounts. Malicious actors exploited stolen credentials and the absence of multi-factor authentication to exfiltrate large volumes of sensitive data belonging to multiple organizations.
Some of the fundamental practices for handling supply chain risks are:

To ensure robust supply chain cybersecurity, you need to think beyond merely managing your third-party risks and develop a comprehensive strategy of cyber supply chain risk management (C-SCRM). C-SCRM can help you enhance business continuity and improve supply chain visibility.
NIST Special Publication SP 800-161r1 and NIST Key Practices in Cyber SCRM can help you create your own C-SCRM program.
9. Enhance your data protection and management
How you manage your business data is critical to your organization’s privacy and security.
You may start by documenting information management processes in a data management policy. Describe how data is collected, processed, and stored, who has access to it, where it’s stored, and when it must be deleted.
It’s also vital to outline your data protection measures in a data protection policy. Build data protection measures based on the key principles of information security:
- Confidentiality — protect information from unauthorized access
- Integrity — make sure unauthorized users can’t modify data at any stage of the data lifecycle
- Availability — ensure authorized users always have access to the data they need
Gartner outlines four key data cybersecurity techniques you can use to implement these principles:

Information security best practices also include implementing insider risk management and data loss prevention solutions to manage data security risks. Managed file transfer platforms can help you securely exchange data with third parties.
To protect your confidential data, also consider implementing the best practices for preventing data leakage through generative AI tools.
10. Implement identity threat detection and response
Recognizing that compromised credentials and accounts are the primary vector for modern attacks, identity threat detection and response (ITDR) focuses on protecting an organization’s identity infrastructure.
ITDR solutions work by continuously monitoring identity-related activities, analyzing behavior patterns, and identifying anomalies that may indicate malicious intent. Once a threat is detected, ITDR tools help security teams respond quickly by isolating affected accounts, enforcing multi-factor authentication, or initiating automated remediation workflows.s.
Gartner
When implementing ITDR solutions as part of your cybersecurity defense strategy, consider these core capabilities:
Identity security posture management
This involves continuously scanning all identities (human and machine) across hybrid environments for misconfigurations, excessive permissions, and dormant accounts.
Advanced threat detection
ITDR threat detection leverages user activity monitoring and behavioral analytics to detect unusual identity activity in real time.
Upon detecting a validated threat, the system must immediately trigger response actions, such as terminating the malicious session, disabling the compromised account, or enforcing additional authentication.
Crucially, ITDR solutions must integrate seamlessly with your broader security ecosystem (for example, with SIEM systems) to provide rich, contextualized identity data. This will enable security teams to efficiently stop lateral movement and complete the investigation and remediation process.
11. Conduct regular cybersecurity audits
Conducting audits regularly helps you assess the state of your organization’s cybersecurity and adjust it if needed. During audits, you can detect:
- Сybersecurity vulnerabilities
- Сompliance gaps
- Suspicious activity of your employees, privileged users, and third-party vendors
The quality of an audit depends on the completeness of data from different sources: audit logs, session records, and metadata. Here’s why you need an audit trail:

Detailed security logs from monitoring solutions can provide you with information about both end users’ and privileged users’ actions, including activity metadata, screenshots, and other insights. This information helps you conduct root cause analysis for security events and identify weak points in your cybersecurity.
If you decide to deploy a UAM solution, pay attention to those that offer reporting on certain types of actions, incidents, users, etc. Reports help to significantly speed up and simplify your audits.
By detecting vulnerabilities with the help of cybersecurity audits, you can prepare a more targeted incident response plan tailored to the findings of your audits.
12. Simplify your technology infrastructure
Deploying and maintaining a large number of tools is expensive and time-consuming. Furthermore, high-resource-consumption software can slow down your organization’s workflows.
Try to choose only one or two comprehensive solutions that contain all the necessary functionality you require. This way, you’ll streamline and simplify your security infrastructure.

If you want to reduce your costs and your response times as well, be sure your solution integrates all the tools you need.
2026 and beyond: Future-proof your security infrastructure with Syteca
2026 will see continued development in cloud security, the increasing use of AI by both attackers and IT defense, a rise in cybersecurity compliance requirements, and a surge in identity threat detection and response tools.
To manage evolving risks, consider implementing the cybersecurity principles and best practices described in this article.
Syteca can assist you.
Syteca is a comprehensive privileged access management (PAM) platform with built-in identity threat detection and response (ITDR) capabilities, offering a holistic and people-centric approach to your organization’s cybersecurity.
Syteca provides your organization with the visibility, control, and responsiveness required to secure your sensitive assets from identity-based and insider attacks. You can implement most of the mentioned best practices for cybersecurity with Syteca’s following capabilities:
PAM for controlling access to your IT infrastructure:
- Detect unmanaged privileged accounts across your environment to take them under control.
- Manage access for all regular, privileged, and third-party users connecting to your IT systems.
- Verify user identities with two-factor authentication.
- Enable secure workforce credential management, with automated password rotation and safe credential sharing for teams.
- Implement just-in-time access provisioning with time-based access restrictions, one-time passwords, and manual approval workflows.
ITDR for visibility and prompt threat response:
- Monitor and record all user activity in your infrastructure in a video format for making informed security decisions and collecting cybersecurity evidence.
- Receive real-time alerts about suspicious user activity for prompt security team response.
- Configure automated system responses to common insider and identity-related threats.
Syteca supports different types of deployment, including SaaS, on-premises, and hybrid environment configurations.
Operating systems supported by Syteca

Windows

Linux/Unix

macOS

Citrix

Microsoft Azure WVD

Amazon WorkSpaces

VMware Horizon

X Windows

Microsoft Hyper-V
Syteca integrates with security information and event management (SIEM) systems, helping you collect all security data in one place and gain a comprehensive view of your cybersecurity.
Want to try Syteca? Request access
to the online demo!
See why clients from 70+ countries already use Syteca.