A single leaked password can lead to devastating breaches. Thus, it’s important to understand that managing your organization’s secrets is not just an IT concern — it’s a business-critical security practice. From your customers’ data to the organization’s financial information, your secrets hold the keys to the most vital areas within your infrastructure. If they are not protected, neither is your sensitive data.
In this article, we break down the real risks of poor secrets management. You’ll discover:
- The lifecycle of secrets — and where most organizations fall short
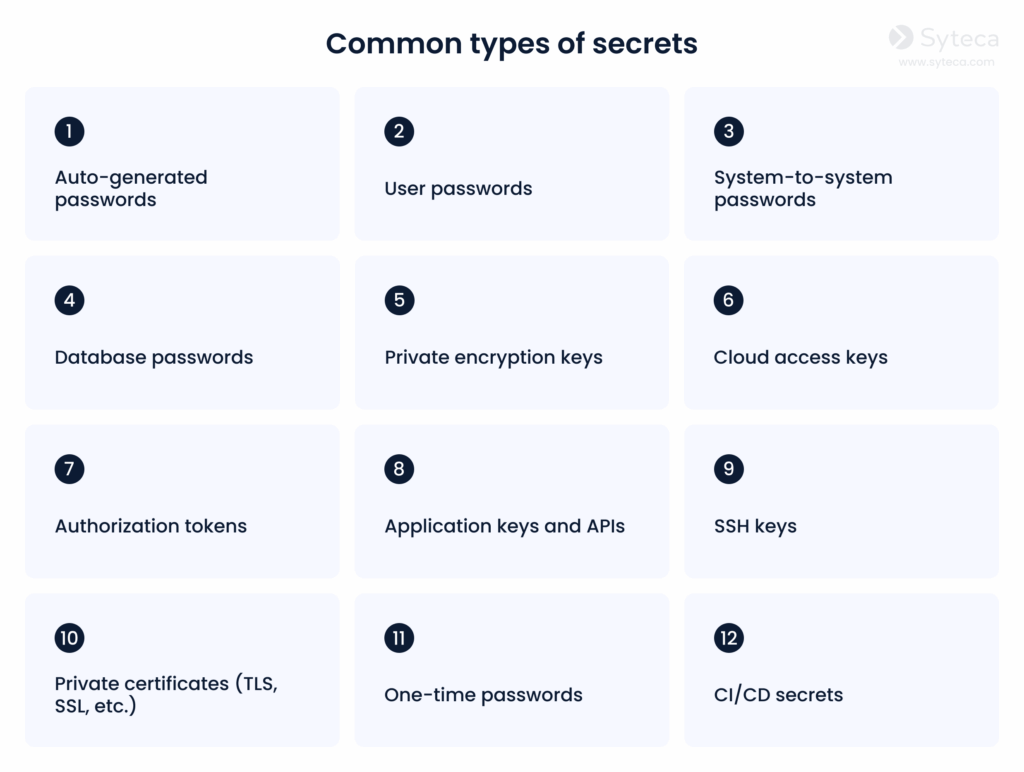
- The most commonly exposed credentials
- The biggest challenges and anti-patterns of secrets management
- 7 actionable practices for securing secrets
- The right tools to support robust secrets management.
What is secrets management?
Secrets management is a centralized approach to controlling who can access which credentials, when, and how. It’s the process of securely and efficiently managing digital authorization secrets, such as passwords, API keys, encryption keys, certificates, and tokens.
Secrets can be used for managing access permissions at both human-to-application and application-to-application levels of interaction.
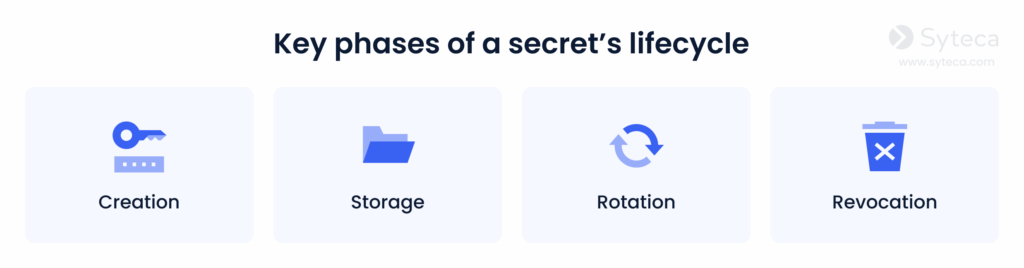
At each phase of their lifecycles, secrets should be protected from unauthorized access, intervention, and manipulation.
With a strong secrets management strategy, organizations can prevent data breaches, business disruption, and unauthorized access to their critical systems.
Explore the power of Syteca now!
See how Syteca can help you meet the requirements of key cybersecurity standards, laws, and regulations.
Why secrets management is important for your organization
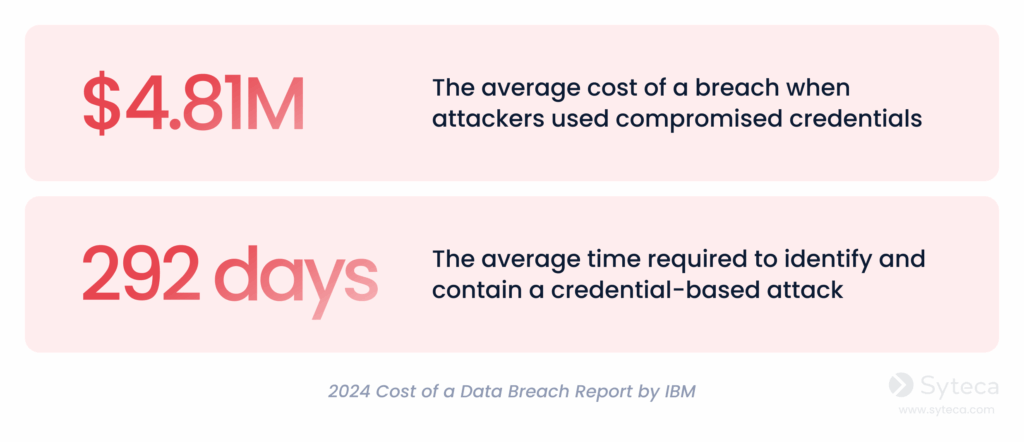
Managing secrets is crucial since misused or leaked credentials are a leading cause of data breaches. According to Verizon’s 2025 Data Breach Investigations Report, stolen credentials are a factor in 22% of data breaches, whereas breaches from credential abuse involving a human element make up 32%. The same report also reveals that 88% of all web application attacks rely on stolen passwords or keys.
Statistics also show that most organizations still fail in protecting secrets. The State of Secrets Management 2024 Survey Report by Akeyless reveals that only 44% of organizations use dedicated secrets management tools, and a startling 70% have suffered disruptions from leaked secrets in recent years.
Almost every company faces secrets-related vulnerabilities, but fewer than half implement secrets management solutions.
Without centralized control, access auditing, automated rotation, and encryption, organizations remain vulnerable to breaches, operational disruptions, and compliance failures.
Secrets management helps to ensure security at three levels:
- Infrastructure security – Protecting user and application accounts, devices, and other network elements from intrusions.
- Security in cloud computing services – Limiting and managing access to cloud accounts and important cloud-based services.
- Data security – Protecting critical systems, storages, databases, and other resources from data compromise.
Additionally, managing and auditing secrets is among the key cybersecurity best practices and requirements of many standards like NIST, PCI DSS, GDPR, and HIPAA.
Still, many teams struggle to implement an effective password management strategy, often hindered by common challenges and anti-patterns.
Secrets management challenges and anti-patterns
Let’s now explore some of the key challenges that get in the way of effective secrets management:
Lack of visibility and inventory
With organizations’ systems, resources, accounts, and applications constantly in flux, the number of secrets and their locations change as well. When secrets are scattered across different environments, it can be difficult for teams to easily see who has access to what. This makes it impossible to enforce credential rotation or detect misuse. For example, a password in a forgotten admin account could pose a hidden risk if not changed regularly.
Lack of a formal secrets policy
Many organizations lack a well-defined secrets management policy. In practice, developers and admins often use their own ad-hoc methods, exchanging passwords through emails, chat apps, shared documents, or spreadsheets. Without company-wide rules, there’s no consistency.
The absence of a formal policy also hinders compliance with regulatory frameworks and increases the likelihood of operational mishaps.
Manual management
According to a survey conducted by Akeyless, 96% of respondents report that organizational secrets are kept outside of dedicated management tools. This slows down the secrets lifecycle management process and can make password storage and sharing less secure. Without automation and centralized control, IT teams are forced to manually manage credentials across different systems, leading to a greater risk of human error, credential abuse, and eventually, compromise.
Moreover, when IT staff manually provision, rotate, and revoke secrets, they have less time to focus on strategic initiatives or higher-priority security tasks.
Hardcoded credentials
Developers often embed secrets directly into source code to save time or simplify workflows. These hardcoded credentials can accidentally end up in public repositories or remain in version control histories, creating major vulnerabilities. For example, any developer with access to a codebase could deliberately extract and misuse hardcoded credentials.
Secrets in the cloud
As more teams adopt cloud platforms and third-party services, secrets like API keys, tokens, and SSH credentials can lack central oversight. This secret sprawl increases the attack surface and makes it nearly impossible for security teams to store secrets securely, rotate them regularly, or even know they exist.
See Syteca in action!
Discover how Syteca can help you mitigate insider risks.
Anti-patterns of secrets management in organizations
Besides the above challenges, many organizations still have one or more anti-patterns in their password management routine.
Common secrets management anti-patterns
It’s quite easy to crack weak or default passwords such as “password123” or “admin” through brute-force attacks.
Storing secrets in plain text
Storing secrets in plain text makes it much easier for an attacker to get into the target system. The only thing they need to do is obtain the needed file with credentials.
Sharing passwords insecurely
When team members email credentials or send them via messenger apps, they significantly increase the risk of secrets being leaked in transit.
Failing to immediately disable or rotate secrets after an employee leaves the organization can expose critical systems to unauthorized access, especially if the employee had privileged permissions.
If secrets are never rotated, they provide standing access to accounts, giving hackers unlimited time to breach them during a credential stuffing attack.
When hackers compromise secrets used for multiple accounts, services, or applications, they can infiltrate multiple systems within your network and cause far greater impact.
organization isn’t that easy. However, implementing the secrets management best practices described below can make the difference.
7 best practices for secrets management
In order to minimize the risk of sensitive data compromise, organizations must pay more attention to the way they manage secrets. Below, we list seven recommendations that can help you build an efficient secrets management system within your organization.
7 best practices for secrets management
1
Create a secrets management policy
2
Discover all accounts that use secrets
3
Automate secrets management processes
4
Enforce RBAC for managing secrets
5
Eliminate hardcoded credentials
7
Monitor, audit, and analyze secrets usage
1. Create a secrets management policy
Determine your secrets management strategy and create a basic secrets management policy for your organization. Your policy should:
- Mandate that all secrets be stored in the secure centralized vault, never in personal files or documents.
- Set strict requirements for password formats.
- Set rules on who can generate secrets, who can access them, how long they remain valid, and how they will be rotated.
- Assign responsibilities (e.g., the security team is in charge of approving vault access requests).
You can expand this list based on the needs of your organization or relevant password security requirements.
2. Discover all accounts that use secrets
Before you can secure secrets, you must identify the accounts that rely on them. Use automated discovery tools to scan your IT environment and uncover all accounts that require credentials, keys, or tokens for access. This process helps build a comprehensive inventory, exposing unmanaged accounts that could put your organization at risk. Once you have gained full visibility of all accounts, you can enforce secrets management across them.
3. Automate secrets management processes
Use secrets management tools (often part of a PAM solution) to automate secret handling. This system should provide an encrypted vault for storing passwords, keys, and certificates. Automate the generation of one-time passwords and schedule rotation of secrets so that credentials are changed without manual effort.
By automating these processes, you eliminate human error and ensure that secrets are never left unchanged for long. Additionally, smooth and automated credential provisioning significantly reduces delays caused by manual requests and approvals. This not only improves operational efficiency but also minimizes downtime and interruptions in critical workflows, boosting overall productivity across the organization.
4. Enforce RBAC for managing secrets
Avoiding excessive permissions is one of the core goals of secrets management. By implementing role-based access control (RBAC), organizations ensure that only authorized users can access specific secrets according to their roles and responsibilities. This limits exposure, minimizes insider risk, and simplifies compliance by maintaining strict access boundaries.
5. Eliminate hardcoded credentials
Proper secret management in development environments is critical. Go through your codebase and configuration to remove hardcoded secrets. Refactor applications so that they fetch credentials from the vault at runtime instead of embedding them. Likewise, change any device or software default passwords to strong ones and store them in an encrypted vault.
A robust application secrets management strategy should ensure that secrets are never exposed, hardcoded, or left unmanaged during development and deployment processes.
6. Use unique credentials
Ensure that all secrets are cryptographically strong and unique for each resource. Every credential should meet high standards of complexity, including sufficient length, a mix of character types, and avoidance of dictionary words or reused phrases. When creating secrets, refer to password security requirements under NIST 800-63, which is considered to be the key standard for password security.
7. Monitor, audit, and analyze secrets usage
Implement continuous monitoring and auditing of all secrets-related activity. A secrets management tool should log every time a credential is checked out, every rotation event, and every access attempt. Ideally, it should also record all sessions that involve the use of credentials.
Review these logs for suspicious patterns, such as repeated access attempts outside normal work hours or from unexpected IPs. Incorporate these logs into your SIEM to detect misuse and perform incident investigations.
Manage secrets effectively with Syteca
Syteca is a comprehensive cybersecurity platform with robust secrets management capabilities. By combining privileged access management (PAM) and user activity monitoring (UAM) solutions, Syteca helps organizations of all sizes address common challenges like secret sprawl, weak passwords, and manual secret handling.
With Syteca PAM, you can:
- Store secrets in a secure vault with military-grade encryption (AES-256, RSA 1024/2048). The vault supports a variety of secret types, including Windows accounts, AD accounts, Unix/Linux SSH and Telnet keys, Web accounts, and MS SQL accounts.
- Securely retrieve secrets for applications from the vault through the Application Credentials Broker (ACB).
- Support role-based access control (RBAC), allowing you to assign roles to define who can view, use, or edit specific secrets.
- Strengthen access control with multi-factor authentication (MFA), ensuring that even authorized users must verify their identity before accessing sensitive credentials.
- Enable secure sharing of credentials between teams under controlled permissions.
- Automatically rotate passwords on schedule or on demand.
- Set time-based access restrictions and approval workflows for accessing secrets.
- Issue one-time credentials for a session to prevent credential reuse.
- Ensure that only one person can use a shared account password at a time thanks to the password check-out feature.
- Automatically scan the network for unmanaged accounts, onboard them into the vault, and change the passwords.
- Record every session that involves the use of credentials.
- Ensure full visibility, security, and compliance by monitoring all actions performed with secrets through the Audit Log.
You can leverage Syteca’s UAM capabilities for quick incident response. Syteca UAM includes a powerful alerting system with an extensive library of rules for detecting abnormal or risky activity in real time. For example, Syteca can trigger alerts on suspicious access activity outside of work hours and immediately block a user, terminate the process, or display a warning message to the user.
Designed to suit both SMBs and enterprises, Syteca supports fast deployment, cloud or on-premises options, multi-tenancy, and integrations with SIEM, ticketing systems, and OTP generator apps.

Unmanaged secrets are putting your organization at risk: Now’s the time to take control
Unmanaged secrets are a silent threat to your organization. Weak passwords, hardcoded credentials, forgotten tokens — they all create entry points for attackers. Without a clear strategy, a secure vault, and automation, your organization remains vulnerable to breaches, downtime, and regulatory penalties.
Nowadays, secrets management is no longer optional — it’s essential. Implementing a modern secrets management system — ideally as part of a broader privileged access management strategy — ensures that credentials are stored securely, accessed only by authorized users, and continuously monitored.
Syteca simplifies it all.
From secure secrets storage and automatic rotation to session auditing and insider threat detection, Syteca gives you full control over who can access what, when, and how.
No more scattered secrets. No more manual work. Just robust security without complexity or high costs.
Want to try Syteca? Request access
to the online demo!
See why clients from 70+ countries already use Syteca.