You may trust the people you work and partner with, but you never know how they really behave and handle your sensitive data within your organization’s network. Each user in your IT infrastructure brings their own security risks. Tracking user activity helps mitigate those risks and enhance your organization’s security.
This article will show you how to set up an efficient user activity monitoring (UAM) process with Syteca. You’ll learn how to:
- Monitor and view user sessions
- Filter user activity monitoring for relevant results
- Configure and view alerts on suspicious activity
- Monitor and block USB devices
- Investigate security incidents
Why monitor user activity?
Your organization may have regular and privileged users, in-office and remote workers, vendors, and third-party service providers with access to your critical endpoints. These may include servers, desktop computers, virtual machines, and embedded devices. Therefore, it may be challenging to detect malicious actions or other insider risks on those endpoints.
Establishing visibility and control over user activity can help your organization manage insider risks and maintain compliance with relevant laws and regulations. Implementing a thorough UAM process with dedicated user activity monitoring software allows you to observe, track, and record user actions within your organization’s infrastructure. Thus, UAM provides visibility into how users interact with sensitive data and systems.
Let’s take a closer look at the benefits of UAM.

Protect sensitive information. Thorough UAM helps detect data leaks and data processing violations. By implementing UAM, you can clearly understand who interacts with sensitive data and for what purposes. For instance, UAM solutions can help you notice a user entering sensitive information into generative AI chatbots, thus, putting it at risk of data leakage.
Swiftly detect and respond to security threats. You can significantly increase your chances of detecting potential signs of security threats and responding to them in a timely manner. For example, user activity tracking software can notify your security team about a user accessing the organization’s systems outside of normal working hours. Upon receiving the notification, security officers can review the user’s actions and act immediately if they recognize a threat.
Simplify incident investigation. UAM ensures thorough documentation of a security incident, which is critical for forensic analysis. By examining user activity logs, session recordings, and reports, you can reconstruct the incident’s timeline and understand its root causes.
Comply with cybersecurity regulations. Many regulations, laws, and standards worldwide require organizations to track user activity to ensure data security and privacy. By implementing UAM, you can meet the requirements of PCI DSS, HIPAA, GDPR, and others, reducing the risk of non-compliance penalties for your organization.
Improve employee productivity. Employee monitoring in the workplace allows you to track performance. Detailed insight into how employees spend their work time enables managers to give accurate feedback and advise employees on how to manage time better. In addition, when employees know they’re being monitored, they are less likely to spend time on non-work-related activities.
Streamline workflows. With UAM, you can detect hitches in your organization’s or specific teams’ workflows and inefficient practices. Understanding which applications or tasks consume too much time can help you optimize processes and allocate resources more effectively.
Read on to see how Syteca can help you reap the benefits of user activity tracking with the functionality it offers.
About Syteca
Syteca is a comprehensive insider risk management platform with robust UAM capabilities that enables organizations to deter, detect, and disrupt security threats coming from within.
You can deploy Syteca software agents to monitor user activity on any type of desktop or server:
Physical and virtual desktops
Syteca supports an extensive list of operating systems and virtual environments:
Platforms supported by Syteca
- Windows
- Linux
- macOS
- UNIX
- X Window System
- Citrix
- VMware Horizon
- Microsoft Hyper-V
- Citrix
- Amazon WorkSpaces
- AWS (Amazon Web Services)
- Azure Windows Virtual Desktops
Syteca’s software agents are lightweight, non-intrusive, and quick to install. Syteca offers a flexible licensing scheme, letting you transfer any license from one endpoint to another in just a couple clicks.
Syteca’s extensive list of features can help your organization establish a thorough yet ethical user activity monitoring process. In the next section, we’ll show you exactly how to track user activity with Syteca.
Leverage Syteca for user activity monitoring
Unlike many legacy solutions, Syteca enables non-intrusive, discreet, and continuous user activity monitoring. Syteca’s software agents work seamlessly without affecting other programs. The platform uses highly optimized formats for storing data and won’t overload your systems.
Syteca addresses user privacy concerns by pseudonymizing user data. The platform replaces user logins, device names, and other personal data, making it impossible to identify a specific user even if the monitoring data becomes compromised.
Syteca has an offline monitoring mode to ensure uninterrupted monitoring. Thus, whenever the Internet connection is lost, Syteca agents continue to collect user activity data and send it to central storage once the connection is restored.
Ultimately, Syteca allows you to capture user activity data, enhancing your security posture without disrupting systems or workflows and compromising users’ privacy or personal data.
Monitoring and viewing user sessions
Syteca monitors all user sessions on endpoints with the Syteca software agents installed. It collects the following information:
- screen capture recordings of on-screen user activity
- visited URLs
- launched applications
- titles of active windows
- typed keystrokes
- clipboard text data
- executed commands & scripts (for monitoring user activity in Linux)
- connected USB devices
On the Monitoring Results page, you can view all monitored user sessions. You can filter them using parameters such as operating system, target workstation, user name, IP address, and remote hostname.
Let’s suppose that you want to watch a specific user’s most recent session. Under the Client Sessions tab, click Who in the filtering options, start entering the username, and select the checkbox in front of the required username.

You will see a list displayed with all of the user’s sessions. Open the latest one by clicking on the Play icon or simply double-clicking it.

When the Session Viewer opens, you can view screen capture recordings on the left side. The right side displays the accompanying metadata on user actions. You can use the Search field in the upper right to search for specific actions.

If the session is still active, you can watch it in real time by clicking the Live button.
Filter user activity monitoring for relevant results
Users within your network might perform thousands of actions daily. Syteca allows you to make user activity monitoring more focused with its filtering functions.
You can configure filtering for specific computers, servers, or their entire groups on the Client Management page.

Suppose you want to disable monitoring for user activity in Word and Excel documents on all endpoints in your organization. Instead of configuring filtering parameters for each endpoint separately, you can open the Client Groups tab and choose the All Clients group.
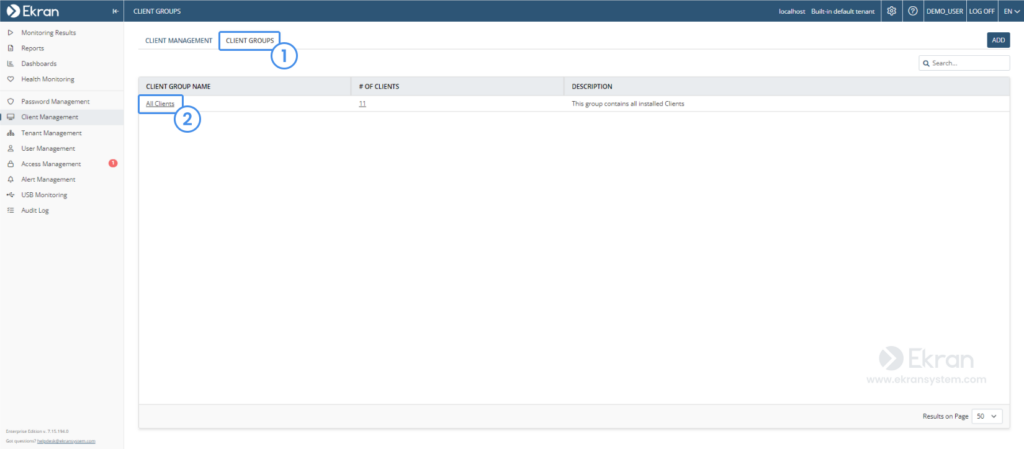
To configure the filtering, you need to:
- Open the Application Filtering tab in Group Settings.
- Choose Monitor all activity except from the Filter State drop-down list.
- Enter “Word;Excel” in the Application Name Contains field.
- Click Finish.

As a result, Syteca will no longer collect user activity data from applications containing the words “Word” or “Excel” in their name.
In a similar way, you can limit user activity monitoring to specific users, time, and remote host IP addresses by specifying the parameters in the corresponding tabs.

You can also configure Syteca to start session monitoring only when users type specific keywords. The recording starts after one of the specified keywords is detected and continues until the session is finished.
To enable this option, open the Keystroke Monitoring tab, check the box for Start monitoring after detecting one of the following keywords, and indicate the keywords in the field below.
Syteca can also be configured to monitor keystrokes only in specific applications by defining related parameters in the Keystroke Filtering group of options.

Configuring and viewing alerts on suspicious activity
Syteca allows you to take a proactive approach to threat management by letting you configure real-time alerts. These alerts notify you about any potentially dangerous user actions so you can respond quickly.
Alerts can be configured on the Alert Management page.

Syteca offers a variety of predefined alerts designed to detect the most common signs of malicious user activity. For instance, if you need an alert for detecting when a user tries to upload files to a cloud sharing service, you don’t need to create it from scratch. All you need to do to use it is find it in the list of default alerts and tailor it to your needs.

You will need to specify:
- Which endpoints to enable the alert for
- The email address to send notifications to
- Necessary automated actions, if needed
In response to user actions that trigger an alert, you can choose to display a warning message to a user, block a user, or kill an application process.
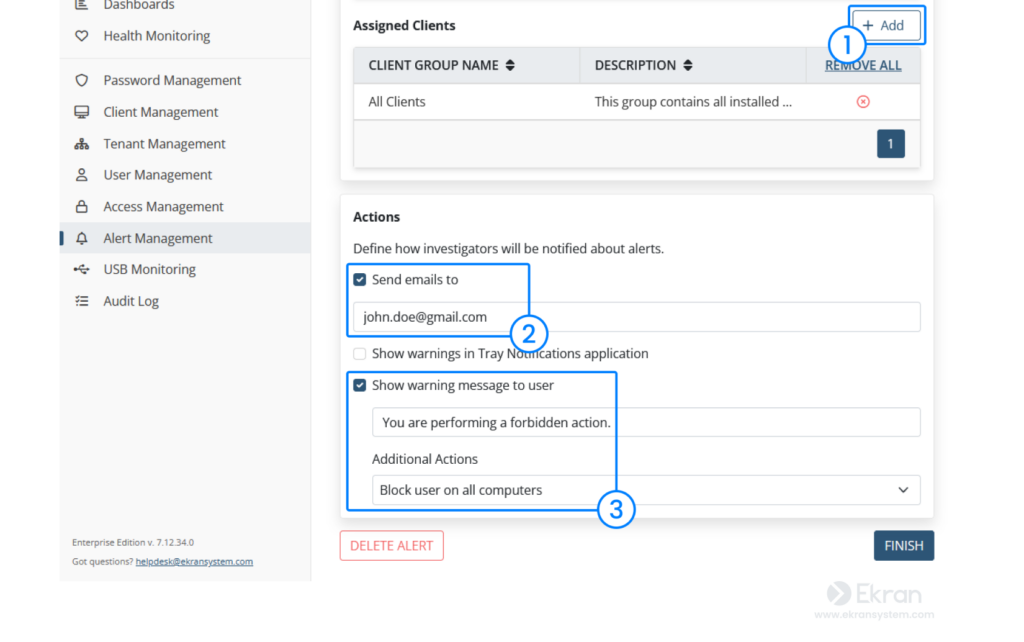
To add a custom alert, click Add in the top right corner and start by filling in the Properties of the alert:
- Select the Enabled checkbox
- Enter a unique name for the alert
- Provide a description of the alert (optionally)
- Specify the risk level (Normal, High, or Critical)

In the Rules section, specify the cases when the alert should be triggered. For this, you need to indicate:
- A parameter for the rule. You can apply the rule to applications, activity titles, usernames, Linux commands and parameters, users or computers belonging to Domain Group, keystrokes, URLs, and clipboard operations.
- A comparison operator. The alert can be triggered when the parameter equals or is like the value you’re comparing it to. Alternatively, it can also be triggered when it doesn’t equal or is not like the specified value.
- A value (to which the parameter will be compared). Here, you can add any value you want to compare the parameter against.

In the Assigned Clients and Assigned Client Groups sections, click Add to select the clients you want to apply the alert to.
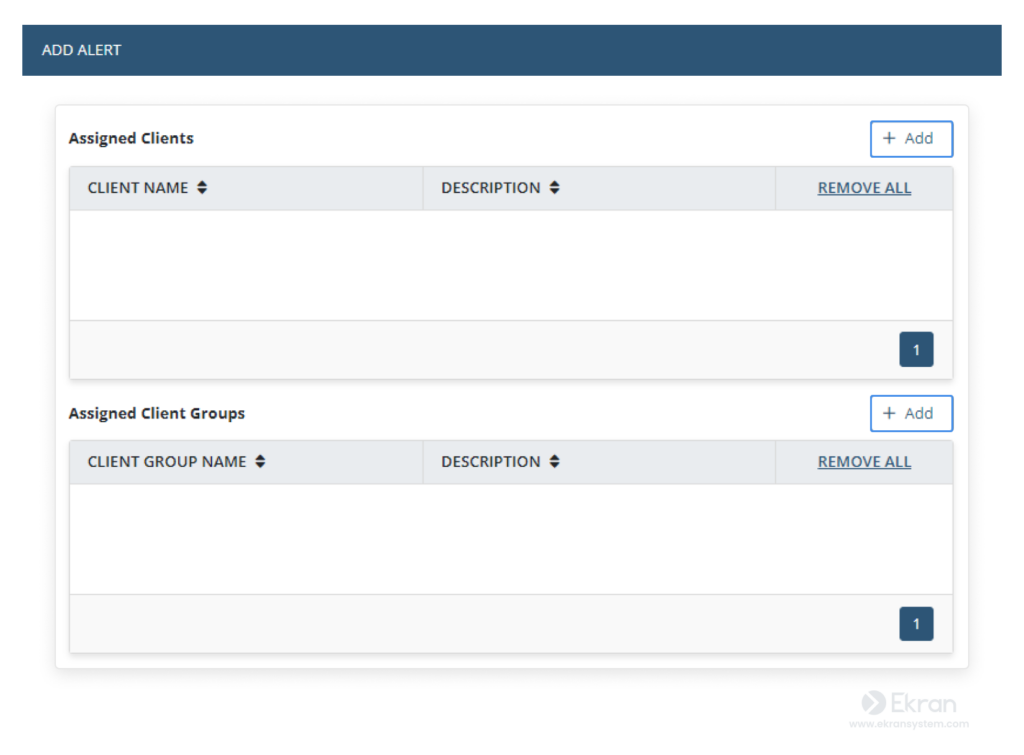
Afterward, you can configure Actions in the same way as in predefined Syteca alerts and click Finish to save the alert.
You can view all triggered alerts on the Alerts tab of the Monitoring Results page and find specific ones by using the Search bar.

Double-clicking a session or clicking the Play button will open the Session Viewer and start replaying the session from the moment the alert was triggered. Potentially harmful activities are marked with an Alert icon on the video progress bar and highlighted in the user activity tracking log.

If the session is still active and you find the user’s actions dangerous to your organization’s security, you can block the user directly from the Session Viewer by clicking the Block User button above the Session Player.

Monitoring and blocking USB devices
Syteca supports two types of USB device monitoring. The first type is automatic. As the name implies, it works automatically without additional configurations. The information related to monitored USB devices is displayed in the Session Viewer.
The second type is non-automatic or rule-based USB device monitoring. In contrast to automatic, rule-based USB device monitoring not only monitors USB devices in the network but can also be configured to notify you about new USB connections or block USB devices.
You can add and edit USB monitoring rules on the USB Monitoring page.

Suppose you need an alert rule for detecting mass storage devices. First, click the USB Monitoring navigation link and click Add in the right-hand corner of the opened page. Then, on the USB Rule Properties tab, select the Enable USB rule option and define properties (name, description, and risk level). Click Next to proceed.

On the Rule Conditions tab, choose the types of devices to monitor by selecting the corresponding checkboxes. If there are any devices you don’t wish to monitor, you can create exceptions for them by clicking Add in the corresponding section.

In the Additional Actions tab, you can configure email notifications upon the connection of mass storage devices. Syteca also enables you to completely block mass storage USB devices automatically upon their connection or until a connection request is approved by an administrator.

Lastly, you’ll need to indicate the clients (endpoints) to which the rule should be applied on the Assigned Clients tab and click Finish to save the rule.

Investigating security events
When a security incident is detected, Syteca can help you understand its context by offering various user activity reports. On the Reports page, you can generate more than 30 different types of reports depending on what insights you’re looking for.

Let’s say you want a report with all security alerts for the specific time period during which a certain incident took place. On the Report Generator tab, you’ll be required to choose a report type from a drop-down list, select the desired file format, and specify the time frame.
Choose the clients (endpoints) or client groups you want to look into. You can then select the users whose data will be included in the report and who can download it. Click Generate Report and then download your report on the Generated Reports tab.

The Alert Grid Report provides information about all alert events in the form of a grid.
While reports can help you get a general understanding of what was going on around the time of the incident, user session recordings can help see exactly how it all happened. Even more conveniently, Syteca allows you to export sessions in a tamper-proof format and use them as evidence in forensic investigations.
To export a specific session, locate it on the Monitoring Results page, open the session, and click the Tools icon at the top right of the Session Player. Then click Forensic Export.

In an opened window, you can choose to export a fragment of a session or an entire session with or without text metadata. If needed, you can even secure it with a password.

Note: To view the exported session, Syteca Forensic Player is required.
Conclusion
Keeping track of user activity is crucial for ensuring IT security and meeting the requirements of cybersecurity regulations, laws, and standards. Syteca is a comprehensive insider risk management solution with many powerful monitoring features to meet your cybersecurity needs.
In addition to providing traditional UAM capabilities, Syteca enhances the monitoring experience with real-time alerts and automated incident response, thus optimizing your security team’s efficiency and reducing potential damage.
Want to try Syteca? Request access
to the online demo!
See why clients from 70+ countries already use Syteca.