People tend to trust those they work with: employees, business partners, subcontractors. But these people, who have access to all kinds of corporate data, don’t always prove worthy of such trust. Insider data theft statistics show that one in four employees won’t think twice before stealing sensitive data from their current company if it will help them sign a contract with a competitor. And according to Verizon’s 2019 Data Breach Investigation Report, 34% of data breaches in 2018 were caused by insiders.
In this article, we investigate the problem of corporate data theft. We start by defining the term, then explore common data theft scenarios. We also go over some of the most effective practices for keeping your secrets safe.
Understanding the nature of insider data theft
Do those you trust the most pose the biggest threat?
What is insider data theft? Data theft can occur both inside and outside an organization and is the most common cause of a data breach. A commonly used insider data theft definition describes data theft as the act of stealing any sort of valuable information stored on corporate devices, servers, and databases.

While the word theft assumes that the act of stealing sensitive information is intentional, that’s not always the case. As with other types of insider threats, the personnel behind the attack may be used by cybercriminals as a weak spot in an organization’s cybersecurity perimeter.
Data theft can be executed unintentionally or intentionally. Those who “steal” valuable information unintentionally usually don’t even know about the data being stolen. For example, hackers may use compromised accounts or personal devices of careless victims to get a hold of the information they need.
The tricky thing is that the moment a hacker enters your network, you can’t tell them apart from legitimate users. The only exception is if you have a sophisticated user activity monitoring or user and entity behavior analytics (UEBA) solution in place.
Using a compromised account, cybercriminals can lurk inside your network unnoticed for weeks, months, or even years. The more access rights the compromised account has, the greater the potential damage.
Those who steal data on purpose, on the other hand, can have different motives, from taking vengeance on their employers to simply gaining financial profit. The individuals most likely to steal data are:
- Departing employees. When someone retires or gets fired, they may take the company’s valuable data with them despite all the NDAs they’ve signed.
- Disgruntled employees. If a team member is mad at their employer for some reason, they may try to harm the company to get revenge.
- Employees conducting industrial espionage. Whether it’s to make money selling your secrets or to get a better job at a competing company, these quiet spies will do their best to take what they want.
Note that this classification is pretty rough. An individual may easily fall into one, two, or all three categories.
Finally, there’s a group of people who many organizations don’t pay enough attention to: third parties. Vendors and subcontractors with legitimate access to your data can also become a malicious insider threat. Just like regular insiders, third parties often work with critical systems and assets. Furthermore, not every organization limits access rights for third parties or the time frame for which they can access the corporate network.
How can you protect your organization against such a threat?
First, you need to know the most common scenarios that cyber thieves use to steal valuable data.
Syteca’s Insider Threat Prevention Capabilities
Common insider data theft scenarios you should know about
They can’t trick you if you know where to look.
In contrast to outsiders, people within the organization know all the ins and outs of your network. Therefore, it’s so much easier for them to apply different insider data theft techniques and steal your data without anyone even noticing. Add some elevated privileges and you have the perfect mix for committing a cyber crime.

5 Levels of User Behavior Monitoring
Let’s take a look at how this all works in practice. Here are just a handful of recent insider digital data theft examples:
- 1. Apple’s stolen trade secrets. In 2018, an Apple employee decided to resign and take some of the company’s confidential data with him. Xiaolang Zhang moved to China and started working for the electric vehicle startup XMotors. However, when the fact of the data theft was revealed, XMotors terminated Mr. Zhang and made an official statement saying that he hadn’t passed any of Apple’s intellectual property to them.
- 2. NSO Group’s stolen software. In 2018, a programmer tried to steal sensitive data and critical cyber technology from NSO Group, an Israeli firm that creates spyware. The man, whose name wasn’t revealed, was planning to sell the stolen secrets on the dark web for at least $50 million. According to statements from NSO Group, the company detected the security issue just in time and no sensitive information was compromised.
- 3. The U.S. Department of Homeland Security’s stolen databases. In 2020, the U.S. Department of Homeland Security started legal proceedings against two of its former employees for illegally collecting, stealing, and destroying critical data. A former acting inspector general of the agency and his subordinate allegedly stole government data and software for at least three years, from 2014 to 2017. The initial plan was to compose a new database out of all the stolen data and sell it to the Department of Agriculture.
As you can see, the outcome is always pretty much the same. Organizations that fall victim to insider data theft risk losing money, clients, intellectual property they’ve worked on for years, and, more importantly, their good name and reputation. Now let’s find out how to prevent intellectual property theft and other types of insider data theft from happening in your company.
Top 5 Real-Life Examples of Breaches Caused by Insider Threats
6 steps to prevent insider data theft
The devil is in the details. Watch closely.
There are many ways to prevent employee data theft:
- Limit access to the most critical systems and data as much as possible
- Monitor every action of all your employees
- Establish strict cybersecurity policies with harsh punishments for any violations
- And more
To protect your data from being stolen, it’s important to come up with a well-balanced action plan, based on a thorough insider threat analysis.
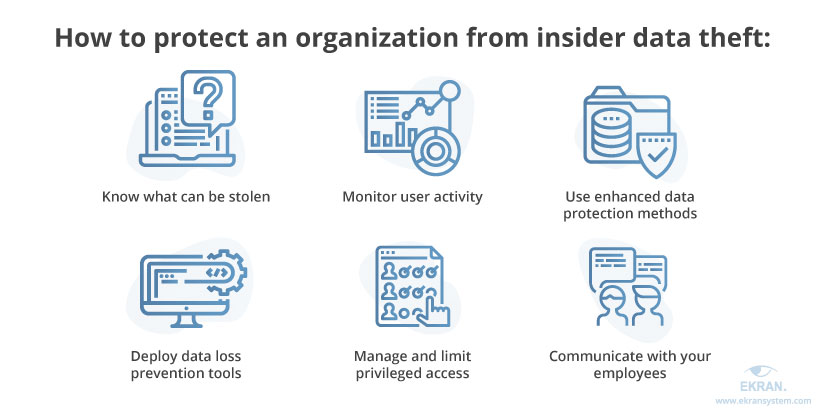
Here’s what you can do to decrease the risk of your valuable data being stolen by an internal actor:
1. Evaluate and classify all data and systems. Know what assets in your organization have the greatest value and, therefore, are most likely to be targeted. Consider creating a list of critical systems and use it to build a thorough and effective data security governance policy. Make sure to re-evaluate this list and the policies based on it every once in a while.
2. Deploy data loss prevention (DLP) tools. It’s not that rare for an employee to tamper with or simply delete critical corporate data, either on purpose or accidentally. Having a DLP solution in place can be quite helpful for restoring stolen or damaged data.
DLP Systems: Pros and Cons
3. Monitor user activity. Keeping an eye on your employees and recording their actions within the corporate network is a great way to figure out what has happened if a cybersecurity incident occurs. To protect critical systems from insider data theft, consider using advanced tools with automatic incident response and UEBA functionalities.

4. Manage and limit privileged access. Users with elevated access privileges are the ones that require the most attention. Whether used by a malicious insider or compromised by an intruder, these users’ accounts open the door to the most sensitive, precious data in your network. Ideally, access privileges should be limited to precisely what someone needs to do their job. Additionally, admin accounts should never be used for routine and non job-related tasks. Finally, it’s critical to make sure that elevated access rights can be downgraded or even revoked completely when necessary.
5. Use enhanced data protection methods. Verifying a user’s identity before granting access to a critical system is vital. Privileged accounts and business-critical operations, systems, and resources should be secured with enhanced data protection technologies:
- Multi-factor authentication (MFA)
- One-time passwords
- Manual access approvals
- USB device management
Also, consider implementing new-generation security models and approaches like the zero trust security model or continuous adaptive risk and trust assessment (CARTA). The zero trust model moves the focus from securing a shared perimeter to securing each and every endpoint, thus eliminating the concept of trusted insiders altogether.
Zero Trust Model: Can Trusting No One Be the Answer to Your Cybersecurity Problems?
The CARTA model, created by Gartner, sees cybersecurity as something adaptive rather than solid. In this model, no entities are trusted by default and access is always based on the current context. Using innovative technologies like UEBA, anomaly detection, and machine learning, and approaches like continuous adaptive trust and zero trust, the CARTA approach can help you handle cybersecurity incidents that can’t be detected with traditional rule-based solutions.
6. Communicate with your employees. Talking to the people you’re working with is crucial for at least two reasons. First, communicating with your employees might help you prevent or effectively resolve personal conflicts — one of the key reasons behind many cases of insider data theft.
Secondly, without such a dialog, you won’t be able to educate your employees on the problem of cybersecurity. But having a well-thought-out policy is just half the battle. You also need to explain to your employees:
- How to act responsibly and securely
- Why it’s so important to follow the rules
- What the consequences can be if they don’t
What Is an Insider Threat? Definition, Types, and Countermeasures
Reduce the risk of insider data theft with Syteca
Syteca is the ultimate insider threat prevention platform that helps organizations secure their critical systems, reduce the risks of account or data compromise, and even improve employee performance.
To prevent data theft by employees, Sytecaprovides you with a rich set of user activity monitoring and access management features. In particular, the user activity monitoring tool allows you to monitor user sessions in real time and record them in the form of audio and video that’s easy to analyze and work with.
For securing privileged accounts, Sytecaprovides advanced privileged access management solution. You can increase the protection of your most critical data, accounts, and services with MFA, require manual login approvals, and add secondary authentication.
To lessen the consequences of any potential cybersecurity event, Sytecaprovides automated incident response functionality. This functionality comes with a wide selection of default alerts, custom notifications, and the possibility to block or terminate users and processes manually and automatically.
Last but not least, Sytecacomes with a third-party vendor monitoring feature that will help you keep an eye on your subcontractors while effectively managing access to your data by third parties and ensuring compliance with industry and local regulations.
Conclusion
While trusting your employees and business partners is essential, every organization should be ready to deal with the problem of insider data theft. To ensure efficient insider data theft prevention, companies need to know what data can be targeted by malicious insiders, who should have access to what within the corporate network, and to what extent. To reduce the temptation of opportunistic attacks and lower the overall risk of sensitive data being disclosed, it’s preferable to implement the principle of least privilege and deploy security models such as zero trust or CARTA.
US-Based Defense Organization Enhances Insider Threat Protection with Syteca [PDF]
Syteca helps organizations mitigate the risks of insider data theft. The platform comes with a rich set of features for verifying user identities, monitoring user activity, managing access and ensuring access granularity, and effectively responding to cybersecurity incidents. Start your 30-day free trial to explore the true potential of Syteca.