Insiders are already within your security perimeter, which makes harmful actions easier to execute and harder to spot. In this article, we analyze seven headline-making insider data breach examples. We also connect each one to practical controls you can implement to enhance your security. Read on and equip yourself with our clear checklist on how to reduce insider risk within your organization.
Key takeaways:
- Insider-driven security incidents occur across various industries and organizations of all sizes, demonstrating that no company is immune. Causes range from poor access control to users’ carelessness.
- Even companies like Google, Marks & Spencer, and Coinbase have fallen victim to significant data breaches, exposing millions of records and critical business information.
- Consequences of these breaches have included not only financial losses but also regulatory fines, lawsuits, and lasting reputational damage.
- Dedicated cybersecurity platforms can help you prevent similar incidents in your organization.
Insider threats and their consequences
Let’s start with the definition of an insider. The National Institute of Standards and Technology (NIST) Special Publication 800-53 defines an insider threat as “the threat that an insider will use her/his authorized access, wittingly or unwittingly, to do harm to the security of organizational operations and assets, individuals, other organizations, and the Nation.”
There are three types of insider threats:
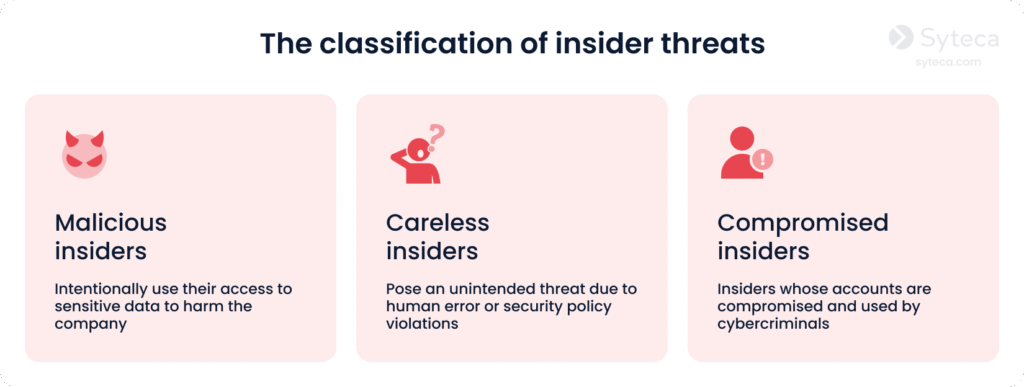
Insider attacks are particularly dangerous for three main reasons:
- Most of the time, insiders’ actions are not malicious, making harmful insider activity difficult to detect.
- Insiders know the weaknesses in your organization’s cybersecurity.
- Insiders know the location and nature of sensitive data they can exploit.
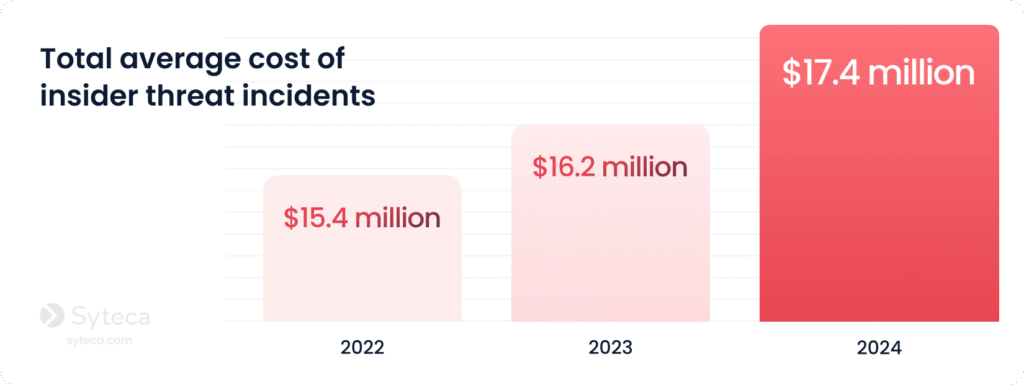
For these reasons, insider attacks precisely target the most sensitive assets and take a long time to contain, resulting in devastating losses for organizations. The total average cost of insider threat incidents rose from $15.4 million in 2022 to $17.4 million in 2024, according to the 2025 Cost of Insider Risks Global Report by the Ponemon Institute.
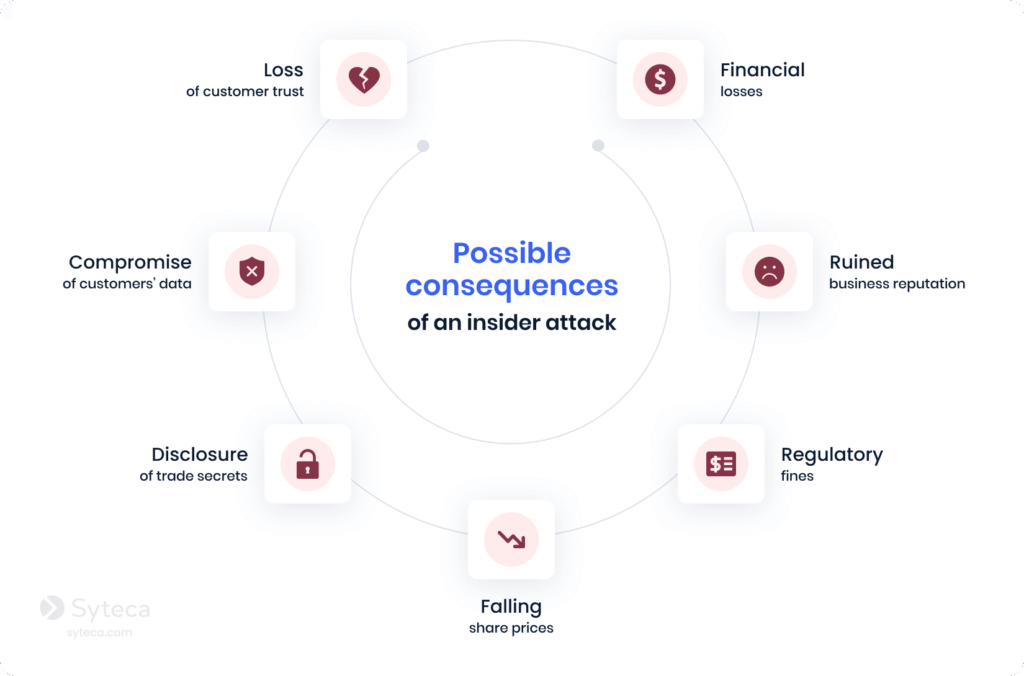
The consequences of cybersecurity breaches caused by insiders can range from penalties for non-compliance with cybersecurity requirements to a loss of customer trust, especially when incidents involve insider fraud or deliberate misuse of access. Here are the most common outcomes among real-life cybersecurity incidents:
In this article, we investigate seven notorious insider threat cases, examine their outcomes, and analyze how these attacks happened. We’ll also show how these internal data breaches could have been prevented.
7 examples of real-life data breaches caused by insider threats
We’ve selected seven examples of data breaches driven by high-profile insider threats. These IT security breach examples illustrate common motives and sources of insider threats. They also highlight how a single incident can significantly harm a company as a whole.
Case #1: Social engineering and ransomware attack on Marks & Spencer
Social engineering attack against a third-party service provider
- Operations disrupted across 1,049 stores
- Online sales suspended for 5 days, with some product lines being offline for 46 days
- Estimated daily revenue loss of £3.8 million and hundreds of millions of pounds in total financial impact
- Customer data exposed
- Temporary drop in market value of £750 million
- Multi-factor identity verification
- User activity monitoring
- Cybersecurity awareness training
What happened?
In April 2025, the Scattered Spider group launched a social-engineering attack on Tata Consultancy Services, Marks & Spencer’s third-party service desk. They impersonated a Marks & Spencer employee and convinced the support staff to reset a password, thereby gaining initial access to the company’s systems. Over time, they deployed ransomware on Marks & Spencer’s VMware servers.
What were the consequences?
Marks & Spencer’s operations across more than 1,000 stores were affected, with online sales suspended for several days and some clothing lines unavailable for over a month. Marks & Spencer reverted to manual stock and delivery tracking, losing roughly £3.8 million per day during the downtime. Additionally, a limited amount of customer data was stolen, including contact details, dates of birth, and partial payment information. The company’s market value fell by about £750 million.
Why did it happen, and what could have prevented it?
This incident is one of many data protection breach examples showing how a single social-engineering call can exploit weak verification controls at a vendor’s service desk. Stronger identity verification protocols, multi-factor authentication for password resets, and continuous monitoring of privileged users could have prevented the compromise or detected it earlier. Additionally, regular cybersecurity awareness training could have helped employees and service providers spot social engineering attacks.
Case #2: Insider theft of AI trade secrets from Google
Insider theft of trade secrets
- P500 trade-secret files stolen
- A decade of research compromised
- Heightened US-China espionage scrutiny
- Continuous user activity monitoring and behavior analytics
- Employee travel monitoring
- Insider threat awareness training
What happened?
In March 2024, Linwei Ding, a Google software engineer, exploited his insider access to steal 500 confidential files containing the company’s proprietary supercomputing data center architecture and AI chip designs.
What were the consequences?
This case of insider data theft is one of the most serious examples of corporate espionage in recent years, exposing more than ten years of Google’s research and development. The incident became a notable data breach case study, alarming national security officials because the stolen data could bolster China’s AI capabilities and undermine U.S. technological leadership. Experts estimate that similar acts of intellectual property theft cost the U.S. economy up to $600 billion annually.
Why did it happen, and what could have prevented it?
Ding allegedly sought profit by promoting himself to Chinese AI firms. He even spent some time in China instead of working full-time in the office in San Francisco. Continuous user activity monitoring, employee travel oversight, and behavioral analytics could have exposed his malicious actions earlier. In addition to these measures, regular insider threat awareness training has been shown to further reduce the risk of intellectual property loss.
Case #3: Data leak by bribed insiders at Coinbase
Abuse of authorized access by customer support agents who accepted bribes
- Data of nearly 70,000 users exposed
- Up to $400 million in remediation and reimbursement costs
- Stock drop of 6%
- Enhanced third-party access control
- Continuous insider activity monitoring and threat detection
What happened?
Coinbase confirmed that a group of overseas support agents was bribed to steal personal data of nearly 1% of its customer base. The attack began in late December 2024 and surfaced publicly when the attackers demanded a $20 million ransom in May 2025.
What were the consequences?
The breach exposed the information of nearly 70,000 people, including IDs and contact details. Coinbase incurred up to $400 million in damages and experienced a 6% decline in share value. The company also devoted resources to fully reimbursing affected customers and enhancing user oversight and fraud detection.
Why did it happen, and what could have prevented it?
Financially motivated insiders exploited legitimate access to exfiltrate data. Such real-life insider threat examples highlight the importance of enhanced access restrictions and insider threat detection tools could have prevented or quickly revealed the scheme.
Case #4: Accidental exposure of British Special Forces identities
Unintentional disclosure of sensitive information
- Exposure of soldiers’ identities
- Risk to ongoing operations and personnel safety
- Regular audits of online publications
- Data protection and cybersecurity training for non-active military personnel
What happened?
In April 2025, it was revealed that the names and ranks of at least 20 members of the UK’s elite Special Forces had been publicly available online for over a decade through two publications linked to the Grenadier Guards.
What were the consequences?
The exposure created a severe security risk for the individuals involved, as terrorists or hostile states could have easily linked names to Special Forces activity. Some soldiers were believed to be on active operations, which heightened the danger for them. The Ministry of Defence removed the files within hours of being alerted, notified the affected personnel, and launched a formal investigation into data-handling procedures.
Why did it happen, and what could have prevented it?
This incident is one of many examples of data breaches caused by insiders, where sensitive documents intended for internal military use were inadvertently published online without protection. Cybersecurity awareness training for all personnel handling sensitive military information would also have helped secure the sensitive data. Regular audits of public content could have prevented the data leak.
See Syteca in action!
Request a demo to see how Syteca can protect your sensitive data from insider-driven breaches.
Case #5: Ransomware attack on Change Healthcare
Ransomware attack enabled by stolen credentials
- Massive theft of PHI and sensitive data (~193 million individuals affected)
- Severe operational outages across hospitals and pharmacies
- Enhanced password management
- Multi-factor identity verification
- Continuous user activity monitoring
What happened?
In February 2024, attackers used compromised credentials to remotely access Change Healthcare’s Citrix portal. After gaining entry, they moved through internal systems, extracted large volumes of sensitive health data, and deployed ransomware nine days later.
What were the consequences?
The attack caused one of the most disruptive healthcare outages in U.S. history. Payment systems, pharmacy operations, and claims processing were delayed for months. Huge quantities of protected health information were stolen, resulting in federal investigations, hefty fines, and regulatory pressure.
Why did it happen, and what could have prevented it?
Change Healthcare’s Citrix portal did not have multifactor authentication enabled, allowing the intruders to bypass security controls. More rigorous password management practices could have prevented credentials from being stolen, while multi-factor authentication could have blocked the attackers’ attempts to access the company’s systems. Real-time monitoring could have helped security officers detect and block the malicious activity.
Case #6: Insider sabotage at OPEXUS
Insider sabotage by two engineers
- 33 databases deleted and 1,805 files stolen
- Weeks of U.S. federal systems outage
- FBI-led investigations leading to the risk of lost contacts
- Strict background checks
- Revoking access immediately upon termination
- Continuous insider activity monitoring
What happened?
In February 2025, two disgruntled OPEXUS engineers, Suhaib and Muneeb Akhter, exploited their insider access to sabotage critical infrastructure, erasing 33 databases and stealing 1,805 sensitive U.S. government files, shortly after receiving notice of their termination.
What were the consequences?
The attack disabled U.S. government tools like FOIAXpress and eCASE, erasing FOIA requests across agencies and drawing the immediate attention of the FBI and DHS. As a result, the Department of Health and Human Services reportedly considered terminating its agreement with OPEXUS.
Why did it happen, and what could have prevented it?
OPEXUS hired the engineers responsible despite past hacking convictions and failed to revoke their access during offboarding. Stronger background screening, automated access termination, and real-time insider monitoring would have prevented the sabotage.
Case study
Eilat Port Monitors the Activity of External Developers Within Their Servers with Syteca

Case #7: Exposure of customer data by a former employee at FinWise Bank
Insider breach by a former employee
- 689,000 people’s SSNs and account data exposed
- Six lawsuits demanding over $5 million in total
- Proper offboarding procedure
- Tightened access management
- Continuous user activity monitoring
What happened?
In May 2024, FinWise Bank experienced an insider data breach when a former employee accessed internal systems after their employment had ended. This incident is an example of security breaches involving improper access management, where the individual accessed personal information belonging to 689,000 customers of American First Finance (AFF), a partner organization. The accessed data included names, birth dates, Social Security numbers, and account details.
What were the consequences?
FinWise faced legal action, with six lawsuits accusing them and their partner of negligence and insufficient security practices. The plaintiffs demand over $5 million in relief and identity theft protection, such as lifetime credit monitoring. The bank’s reputation was damaged, and the incident attracted the attention of industry regulators.
Why did it happen, and what could have prevented it?
The breach occurred because a former employee retained valid access, and the bank lacked visibility into account use. Better offboarding procedures with immediate access revocation and continuous activity monitoring could have mitigated the damage.

In the next section, we show you how Syteca’s insider threat detection and prevention capabilities can help you manage the risk of experiencing a data breach like those we’ve analyzed above.
As real-world incidents show, insider attacks can strike any organization, often with devastating impact. But with the right tools, you can detect and respond to insider threats early.
Syteca is a privileged access management (PAM) platform with identity threat detection and response (ITDR) at its core. The platform allows you to protect the inside perimeter of your organization against threats through these capabilities:
Enforce granular access controls and grant time-bound permissions.
Track third-party vendors’ activity to ensure their adherence to security policies and minimize security risks.
Syteca is quick and easy to deploy, which allows you to start enforcing insider threat protection faster. Pricing can be tailored to fit your budget, operations, and evolving cybersecurity needs. With Syteca, you can comfortably scale as your organization grows.
Syteca is your reliable partner in mitigating insider risks.
Want to try Syteca?
Request access to the online demo!
See why clients from 70+ countries already use Syteca.