In 2020, remote work became not just a trend but a must for many companies. Yet ensuring secure telecommuting turned out to be a challenge for cybersecurity teams: Remote employees tend to use insecure tools, work in unprotected environments, and mismanage sensitive data. All of this increases the risk of insider threats.
In this article, we take a close look at the challenges remote employees bring and the risks they can pose to your organization. We also offer six best practices for insider risk management.
Insider threats vs insider risks
We’ve all heard of insider threats, but are insider risks any different?
In everyday speech, we often use the words “threat” and “risk” as synonyms. However, when it comes to risk management, they’re not the same.
When we talk about insiders, a threat is the possibility that a user with authorized access to an organization’s sensitive resources may misuse that access to harm the organization. Insiders risks mean the potential loss or damage that an organization may experience as the result of an insider threat.
For example, say an organization experiences a threat in the form of employees leaking trade secrets to competitors. In this case, the organization faces the risk of severe financial losses as a result of losing its competitive advantage on the market.

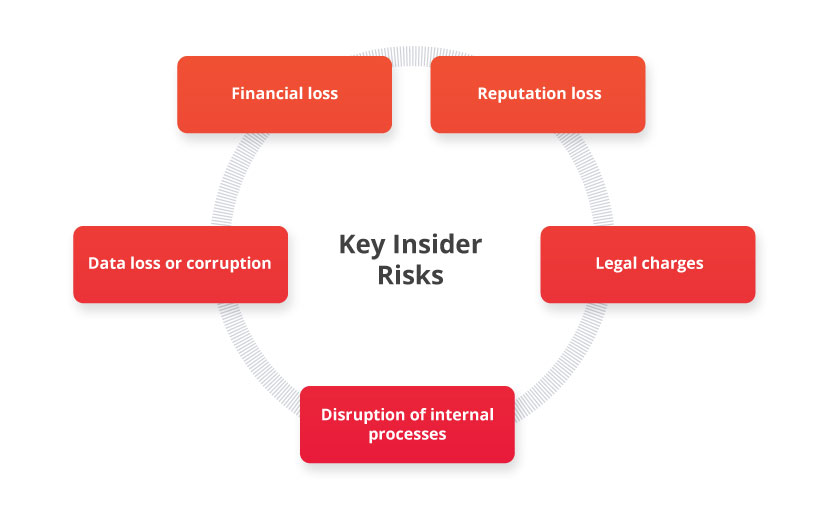
Here are the key risks organizations experience because of malicious insider activity:
- Financial loss — This can include remediation costs, compensation for parties affected by an attack, fines for non-compliance with laws and regulations, etc. The bigger the impact of an attack, the more money a company has to pay to remediate its effects.
- Reputation loss — Сurrent and potential customers will likely lose trust in a company that can’t keep their data safe, and this trust is extremely hard to regain.
- Data loss or corruption — Some insider activities include editing or deleting sensitive data. Restoring lost data may be challenging or even impossible.
- Legal charges — Insider activity can result in court hearings because of claims against an organization, theft of intellectual property, failure to comply with cybersecurity and other regulations, and other reasons.
- Disruption of internal processes — When an insider attack happens, an organization needs time to assess the damage, remediate the incident, and get back to normal operations.
Both in-house and remote employees can pose threats that may lead to the risks described above. But why pay special attention to telecommuters? Let’s discuss the key reasons in the next section.
What Is an Insider Threat? Definition, Types, and Countermeasures
Why are remote employees dangerous?
Remote work isn’t just a temporary trend in 2020. According to a survey by Gartner, 82% of company leaders plan to allow their employees to telecommute several days a week after the COVID-19 pandemic. Nearly half (47%) are willing to let employees keep working remotely full-time.
This might be good news for regular employees but not for cybersecurity teams. For them, telecommuting presents the continuous challenge of establishing and maintaining secure remote practices. And this challenge is a serious one: 73% of vice presidents and C-level IT leaders believe remote workers pose more security risks than their office-based colleagues, according to an OpenVPN survey.
How different are remote insiders from office-based insiders?
IBM and Morning Consult surveyed employees who recently started telecommuting and discovered that many of them use unsafe practices while working:

7 Third-Party Security Risk Management Best Practices
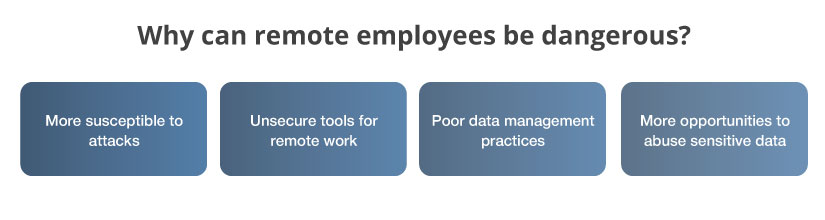
Remote employees have a higher chance of putting their companies at risk than in-house employees for four key reasons:
- More susceptible to attacks. Compared to in-house employees, telecommuters are often less protected. First, they work outside the protected perimeter, which means that corporate SIEM, DLP, and firewalls systems don’t protect them. Second, remote workers usually use personal devices that are harder to secure and monitor than corporate devices. Finally, telecommuters connect to home and public Wi-Fi networks, which often aren’t even protected with strong passwords. These factors make remote employees vulnerable to various hacker attacks.
- Use of unsecure tools. To ensure business continuity, IT teams usually select a limited scope of secure third-party applications for tasks like video conferencing, data sharing, emailing, etc. However, instead of those selected apps, telecommuters may use unapproved tools that are likely to be outdated and full of vulnerabilities.
- Poor data management practices. While working from home, some employees prefer to download sensitive data to their personal devices. This is a common situation within organizations that secure access with a solution like a VPN, as such solutions may be slow and uncomfortable to use. However, storing corporate data on personal devices is not the wisest choice for three reasons: locally stored data may be accessible to hackers, the company has no control over this data, and such practices may violate compliance requirements.
- More opportunities to abuse sensitive data. Telecommuters work in a less protected environment but have the same level of access to sensitive data as their office colleagues. If a telecommuter has malicious intent, it’s easier for them to steal or leak data, engage in espionage, or practice insider trading while leaving little to no evidence.
At the start of the coronavirus pandemic, many companies deployed ad hoc cybersecurity solutions to provide employees with the ability to work remotely and minimize workflow disruptions. Since telecommuting is here to stay, it’s important to transform these efforts into a consistent cybersecurity system. Let’s see which best practices for managing insider risk coming from telecommuters.
Remote Employee Monitoring: How to Make Remote Work Effective and Secure
6 best practices to manage insider risks posed by telecommuters
Controlling and mitigating insider risks may seem like a time-consuming process at first. You’ll need to deploy new security tools, implement insider risk management best practices, and educate telecommuters on both. It’s also important to build an insider threat program to prevent and detect insider threats effectively.
Here are the six insider risk management activities that will help you do it:
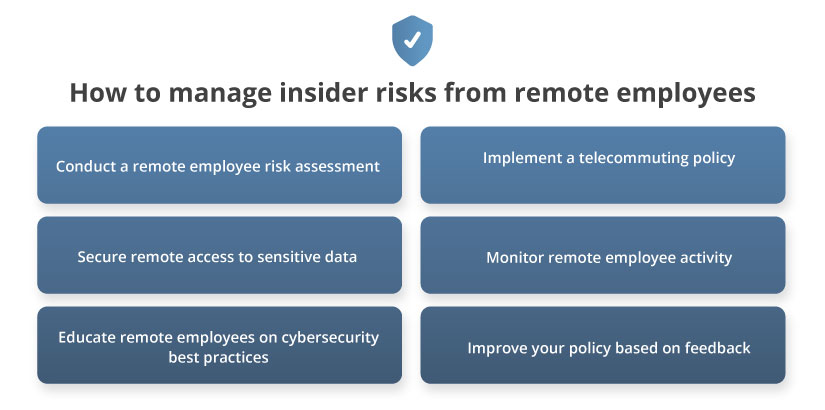
1. Conduct a remote employee risk assessment
Risk assessment in cybersecurity should not be underestimated. It can help you identify all the threats, vulnerabilities, and risks your organization may experience, the likelihood of their occurrence, and their possible impacts. It is the first step of the insider threat risk management process. Estimating risks coming from remote employees can be a standalone process or part of an overall cybersecurity risk assessment.
The key reason to conduct a risk assessment is to identify the weakest parts of your cybersecurity and improve them to reduce insider threat risks. When assessing risks coming from remote employees, pay attention to:
- High-risk users working remotely. Do your administrators, privileged users, or C-level officers telecommute?
- The level of control over sensitive data. Do you know for sure which remote users access which data? Do they store it in a protected environment or on a family laptop?
- Tools used for telecommuting. Have you recommended secure tools for your remote employees to hold meetings, communicate, share data, and access sensitive resources?
- Possibility of an insider attack. Do you have all the tools to detect and stop an attack in time? Have you created an insider threat response team?
- Previous security incidents. Has your organization ever experienced an insider threat? Have you revised your current cybersecurity policy and implemented extra measures to protect the organization from facing similar threats in the future?

How can Syteca help?
The quality of risk assessment depends on the accuracy of data on user activity and the number of exploitable vulnerabilities in an organization’s cybersecurity. Using Syteca’s activity monitoring and recording features, you can gather the information needed to detect and assess possible threats coming from your remote employees.
Insider Threat Risk Assessment: Definition, Benefits, and Best Practices
2. Implement a telecommuting policy
A telecommuting policy is a formal document that details all the conditions for working remotely in your company. It should answer all your employees’ questions on telecommuting.
A telecommuting policy usually includes:
- A list of employees that can work remotely full-time and part-time
- The means to ensure business continuity, including working hours, reporting procedures, obligatory meetings, etc.
- Communication guidelines
- Equipment that an organization provides to remote employees and how to get it
- Cybersecurity tools that remote employees have to install and configure (by themselves or with help from an administrator) on the devices they use for work
- The consequences of ignoring the requirements of the telecommuting policy
It’s best to team up with the HR and legal departments in your organization to create a comprehensive policy.
3. Secure remote access to sensitive data
Remote access to sensitive data is a major point of vulnerability for any organization. For a hacker, it’s easier to breach the personal devices of remote employees instead of hacking a corporate data center. That’s why securing remote access is one of the most important steps in setting up telecommuting processes.
First, you need to secure the connection between the remote user and the sensitive resource. The most common way to do that is to deploy a VPN.
Then you have to ensure that the person trying to connect is really your employee, not a hacker, family member, or a cat accidentally pressing the right keys. You can do that with an identity management solution.
When a connection is established, users should be able to access only the data they need to do their jobs. Look closely at approaches like the just-in-time approach, the principle of least privilege, and the zero trust model and pick the tools and practices that serve the needs of your organization.
How can Syteca help?
Syteca has a robust toolset for identity and access management. When a user connects to a secured network or resource, you can verify their identity with the help of Syteca’s multi-factor authentication tool.
With Syteca, you can also configure access rights for each user or user group, securely manage credentials, and, when necessary, manually approve requests to access the most critical assets.
Privileged Access Management
4. Monitor remote employee activity
An employee monitoring system is a great way to detect incidents in time and make sure your employees follow cybersecurity best practices. It helps you answer these questions:
- Do telecommuters use third-party applications recommended by cybersecurity officers?
- How do remote employees manage sensitive data?
- How productive are remote employees?
Note that before deploying a monitoring solution, it’s best to inform your employees of:
- The reasons to deploy a monitoring solution
- Actions and data that will be monitored
- How your organization will handle the collected monitoring records
The goal is to help telecommuters realize that monitoring software won’t harm their privacy and is not a sign of distrust on the part of management.
How can Syteca help?
The user activity monitoring (UAM) functionality in Syteca provides you with full visibility into the actions of remote users, whether you want to watch user sessions in real time or review records. With a vast amount of metadata, it’s easy to find an event, establish its context, and assess whether user actions violate the company’s policies or put data at risk.
To keep you notified of suspicious activity, Syteca sends an alert each time a user triggers a default or custom security rule. Once security officers receive a notification, they can review the incident and block the process or the user.
Employee Monitoring Software
5. Educate remote employees on cybersecurity best practices
You should always make sure your employees have the knowledge they need to work securely. However, remote employees need more intense cybersecurity training than in-office employees because they work outside the protected perimeter.
When creating an educational program for your telecommuters, make sure to include:
- Clear instructions on how to use the deployed cybersecurity tools
- Practices to handle data when working with personal devices or connecting to private or public networks
- Typical cases of hacking and social engineering attacks and ways to avoid them
- People to contact when telecommuters have security-related issues or questions
How can Syteca help?
With Syteca’s UAM features, you can review remote user sessions and find out if telecommuters work in a secure manner. The software also allows you to configure custom security rules and show warning messages when an employee breaks one of them. You can configure these messages to be educational and explain to employees which of their actions are insecure and why.
6. Improve your policy based on gathered feedback
Any cybersecurity measures you implement have to be not only efficient but also comfortable and non-disruptive for your remote employees. If they’re inconvenient and disruptive, there’s a high chance telecommuters will ignore your policies and won’t use the recommended software.
Since it’s impossible to track and punish each policy violation, it’s best to establish an environment of trust where remote employees can suggest improvements to the telecommuting process.
An HVAC Service Provider Secures Data and Maintains Employee Productivity after Switching to Remote Work
Conclusion
The rapid switch to remote work in 2020 was challenging for many companies. But it’s crucial to go one step further and establish a consistent system and learn how to manage insider risks originating from remote employees.
You can start by conducting a remote employee risk assessment. In this way, you’ll know what new risks and threats your organization may face with the increase in telecommuting. Next, consider implementing a clear telecommuting policy, establishing or improving user monitoring routines, and taking proper precautions to secure remote access to your company’s sensitive data. Regular employee training and cybersecurity policy updates are also important.
Deploying Syteca can help you implement most of these best practices. Start monitoring remote employees and managing their access with our solution!