Active Directory (AD) is central to identity and access management. However, when poorly managed, it can be exploited in ways that could compromise your organization’s sensitive assets and operational resilience. In this article, we discuss possible threats to Active Directory, provide an essential AD audit checklist, and explain how to strengthen your security with privileged access management and monitoring.
Key takeaways:
- Active Directory helps manage authentication and access to critical organizational assets, making it a prime target for cyberattacks.
- Common vulnerabilities such as weak passwords, default AD settings, privilege creep, and unpatched systems increase the AD attack surface.
- Conducting regular AD audits helps organizations detect misconfigurations, inactive accounts, and privilege misuse, while ensuring compliance with regulations like SOX, the GDPR, and HIPAA.
- Privileged access management strengthens AD security by controlling, monitoring, and securing privileges, thus minimizing lateral movement and privilege escalation risks.
- Syteca PAM integrates with Active Directory to automate account discovery, password rotation, and access control, as well as offering session recording and prompt incident response.
What is Active Directory, and why is it a security target?
Active Directory, or AD, is a service that enables administrators to manage permissions and access to network resources. Developed by Microsoft for Windows domain networks, AD allows users and computers to access specific applications and files based on their identity.
Since admins use Active Directory for user authentication and authorization, it’s a common target for cybercriminals. Malicious actors, both external and internal, may target AD because it can help them access an organization’s user accounts, databases, files, applications, and sensitive data.
Common Active Directory security threats and vulnerabilities
With the potential of Active Directory and privileged user accounts to give so much power to malicious actors, it’s no wonder that phishing and abuse of valid account credentials are among the top initial attack vectors, according to the X-Force 2025 Threat Intelligence Index by IBM Security.
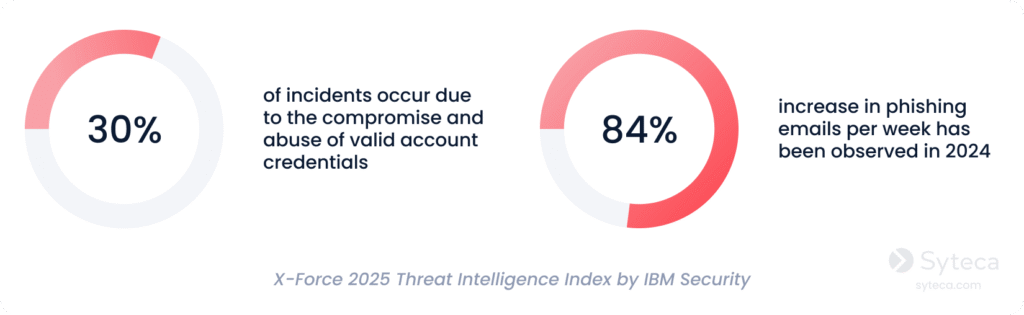
Given that, let’s take a look at common Active Directory vulnerabilities and threats:
6 factors undermining Active Directory security
Unpatched vulnerabilities
1. Default settings. Microsoft provides Windows Active Directory with predefined security settings, but they may not be enough to protect your IT environment. Hackers are familiar with default settings and can use them to find and exploit AD security gaps.
2. Privilege creep. Active Directory users and user groups may accumulate unnecessary access rights over time due to job changes or new projects. This uninterrupted high-level access provides many opportunities for malicious internal actors and external attackers to break in.
3. Weak passwords. Hackers often use brute force attacks on AD environments, guessing simple passwords for administrative accounts. If those passwords are easy to crack, your organization’s security could become compromised.
4. Unpatched vulnerabilities on AD servers. If you fail to update software on time, hackers can find their way into your organization’s IT environment by exploiting unpatched applications and operating systems on AD servers.
5. Hybrid environments. In hybrid and cloud environments, Active Directory cross-domain integration faces challenges of poor security oversight, inconsistent policy enforcement, and misconfiguration, all leading to potential breaches.
6. Lack of segmentation. If users, systems, and permissions are not properly isolated within your environment, AD attackers could move laterally across the network, creating new pathways and escalating privileges.
If not addressed, all these factors and vulnerabilities can significantly increase your organization’s attack surface, making it susceptible to the following Active Directory threats:
Common threats to Active Directory
Credential theft and forgery attacks
Credential theft and forgery attacks. These attacks involve exploiting Active Directory’s authentication mechanisms to steal or forge credentials. Techniques such as golden and silver ticket attacks, pass-the-hash attacks, and kerberoasting target Kerberos tickets or password hashes to bypass authentication.
Insider threats. Insider threats occur when your employees, third-party vendors, or partners misuse their valid AD credentials. Examples include users copying sensitive data to personal devices, system administrators abusing their elevated access, and employees exposing credentials through phishing attacks. With 60% of all data breaches involving a human element, as stated in Verizon’s 2025 Data Breach Investigations Report, insider threats must be taken seriously.
Supply chain attacks. Malicious actors can exploit the trust you have in your supply chain entities to infiltrate your Active Directory. Supply chain exploits involve attackers entering the organization’s IT environment through third-party vendors, software dependencies, or compromised update patches.
So, how to secure Active Directory?
Effective Active Directory protection involves implementing a combination of the following measures:
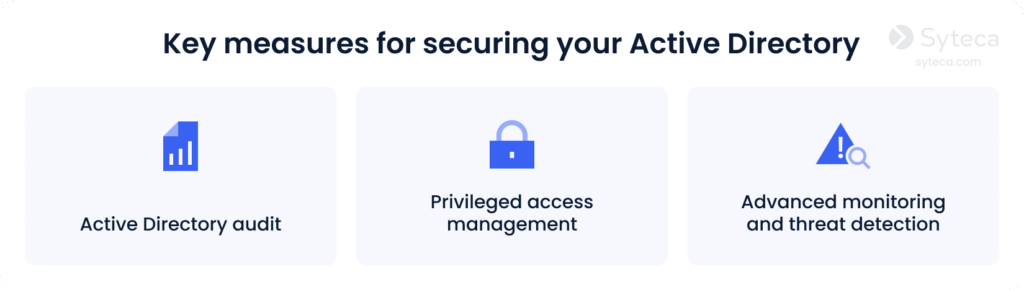
Let’s start by exploring the basics of the Active Directory auditing process and best practices for it.
Active Directory audit: Checklist and best practices
The Active Directory auditing process aims to evaluate the overall security of your AD services. This comprehensive process goes beyond simply collecting data; it involves strategically monitoring and analyzing activity within your AD infrastructure.
Why audit Active Directory?
When conducted properly, Active Directory audits can help you improve security, promptly identify and respond to threats, and maintain smooth IT operations.
Auditing Active Directory can help your organization reduce security risks, such as:
- Deeply nested groups that can be challenging to track. AD offers almost unlimited possibilities to create nested groups (groups that are members of other groups). And since nested groups inherit the same access rights as parent groups, there’s a risk of users having unnecessarily extensive permissions.
- Directly assigned permissions that attackers can exploit to gain access to network resources.
- Circular nesting that can cause security issues, such as providing users with too many application permissions or causing applications to crash.
Security auditing of Active Directory can also help your organization meet IT cybersecurity requirements. The most common standards, laws, and regulations obligate organizations to secure sensitive client data and control access to it. A dedicated SOX, GDPR, HIPAA, or SOC 2 compliance tool with AD auditing capabilities enables you to track actions (logging on and off, accessing files and folders, etc.) performed by users across your IT infrastructure.
What should Active Directory audits report on?
By learning how to audit Active Directory and what to pay attention to, you’ll gain valuable insights into user activities and system changes. This can help you detect suspicious behavior and prevent potential security breaches.
Here’s a checklist of things your security officers should focus on when they audit Active Directory:
Active Directory audit checklist
Granting, modification, or elevation of privileges
Creation, modification, and deletion of user accounts
Dormant, orphaned, and inactive accounts
Default Active Directory settings
Replicated Active Directory data
Failed authentication patterns
See Syteca in action!
Discover how you can manage and monitor access with Syteca.
Now that you know what to pay attention to in your Active Directory audits, let’s dive into the best practices that can be derived from this knowledge.
Top 7 Active Directory auditing best practices
Every organization has its own strategy for securing Active Directory with an audit, but the most effective best practices for Active Directory auditing are as follows:
1
Review and change default security settings
2
Limit the number of privileged users
3
Audit account logon and logoff events
4
Remove inactive and obsolete accounts
5
Use real-time Windows auditing and alerting
6
Ensure AD backup and recovery
7
Patch all vulnerabilities regularly
1. Review and change default security settings
Out-of-the-box AD security settings might not be sufficient for your specific needs. To strengthen the security of Active Directory, regularly review and adjust your settings related to password complexity, account lockout, and group membership permissions.
2. Limit the number of privileged users
Privileged access permissions give unrestricted power to users, compounding the risks of privilege abuse and misuse. Granting privileged access to a limited number of individuals minimizes the risk of malicious activity and reduces the attack surface. Implement the principle of least privilege by giving users only the permissions they need to perform their assigned tasks.
3. Audit account logon and logoff events
One of the most effective best practices for maintaining Active Directory is monitoring user logon and logoff activity to identify suspicious attempts, such as unauthorized access from unusual locations or logons outside of regular work hours. This helps detect potential security breaches and enables the investigation of suspicious user behavior.
4. Remove inactive and obsolete accounts
Inactive and obsolete accounts pose a security risk, as they can be exploited by attackers. Regularly conduct account discovery scans and user access reviews to identify and disable unmanaged privileged accounts. This will minimize security gaps and improve overall AD hygiene.
5. Use real-time Windows auditing and alerting
While performing scheduled AD audits, you can miss critical events happening in real time. Incorporating real-time auditing and alerting capabilities into your security system allows you to receive immediate notifications of potential security threats. This results in faster response times and better risk mitigation.
6. Ensure AD backup and recovery
Regularly back up your AD data to ensure you have a reliable recovery point in case of cyberattacks, accidental deletions, and other incidents. Your backups will enable you to quickly restore essential data and minimize possible downtime.
7. Patch all vulnerabilities regularly
Unpatched vulnerabilities enable cyber attackers to gain unauthorized access to your systems and sensitive data. Install security updates frequently to address software vulnerabilities and minimize the risk of exploitation.
In addition to an AD audit, you can also leverage best practices for privileged access management to enhance the security of your Active Directory environment. Let’s take a closer look at what PAM is and how it can benefit your AD security.
Privileged access management (PAM) for Active Directory security
Privileged access management (PAM) is a comprehensive set of cybersecurity strategies and technologies for establishing control over privileged access across the IT environment.
Why use PAM to protect Active Directory?
Establishing robust privileged access management is a must in order to secure an organization’s data and systems and eliminate various AD-related risks. AD itself is managed by privileged accounts, so securing them is vital.
System administrators often center privileged access management solutions around an organization’s Active Directory environment as a way of delegating privileged access from a centralized, monitored location.
Using PAM tools for Active Directory security helps you to:
- Identify and manage accounts with elevated privileges
- Detect users with unnecessarily broad access rights
- Centralize access management
- Reduce the risks of privilege misuse and data leaks
- Implement a zero-trust approach
- Minimize lateral movement and privilege escalation
PAM implementation roadmap
When implementing organizational and technological PAM measures, you can use this basic roadmap as your guide:
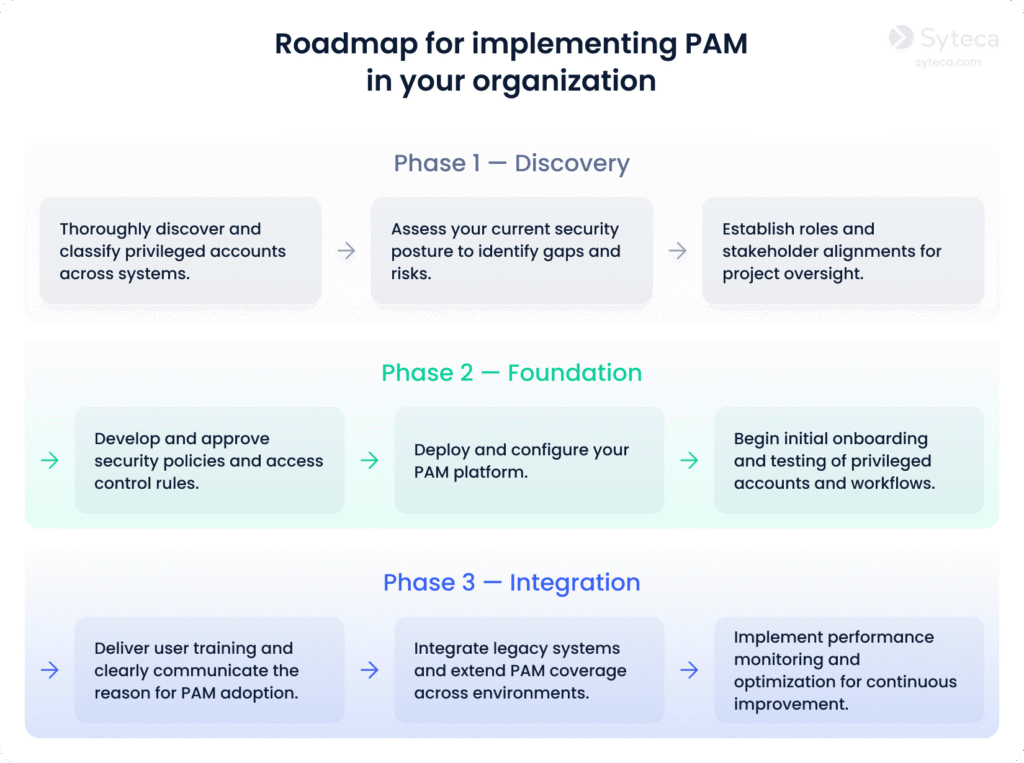
A PAM implementation roadmap can provide you with a structured path to strengthen control over privileged accounts and reduce security risks.
6 best practices for securing Active Directory with PAM
To get the most out of leveraging PAM to secure your AD environment, let’s explore six helpful best practices for establishing proper privileged access management:
1
Keep an inventory of all privileged accounts
2
Balance privileges with user needs
3
Use multi-factor authentication
4
Choose an appropriate access control model
5
Secure employees’ passwords
1. Keep an inventory of all privileged accounts
Active Directory monitoring best practices include increasing visibility and managing privileged accounts. Keeping an inventory of all privileged accounts will help you:
- Know which users and systems have access to sensitive data
- Check whether certain users still need privileged access
- Remove elevated access rights once a user no longer requires them
The list of privileged accounts is determined by the access control solution or directory service you are using. In Active Directory, default groups of privileged accounts include:
However, there can be other groups of privileged accounts within your organization’s infrastructure.
Manually compiling and managing a list of privileged accounts is inefficient, especially for a large organization. Instead, use a cybersecurity tool that automatically discovers and displays all privileged accounts. Be sure to also follow system administration best practices to protect your privileged user accounts.
Syteca is a comprehensive cybersecurity platform that secures your IT perimeter from insider threats. Syteca PAM integrates effectively with Active Directory and includes an account discovery feature, which allows you to identify all unmanaged privileged accounts within your IT environment, safely onboard them, and rotate their passwords.
Explore the power of Syteca now!
Discover how Syteca can protect your IT perimeter from the inside.
2. Balance privileges with user needs
The fewer access privileges you grant a user, the lower the risk they’ll misuse these privileges and cause an incident. However, it’s often difficult to minimize privileges without impacting employee efficiency.
To overcome this challenge, consider implementing one or more of the following techniques:
3 techniques for minimizing standing privileges
No one is trusted by default. Access is granted only to authenticated and verified users.
Users can access only the information and resources they need within their scope of responsibility.
Access to sensitive systems and resources is granted only to appropriate users, for a valid reason, and for a limited time.
Syteca PAM allows you to minimize standing privileges in the following ways:
- Approve access to critical endpoints manually
- Limit the time of user sessions
- Grant one-time passwords to provide secure access to sensitive endpoints
- Integrate ticketing systems to validate the reasons for privileged access requests
- Check out passwords so certain secrets can only be used by one user at a time
3. Use multi-factor authentication
Even strong credentials can be compromised, so it’s always best to enable multi-factor authentication (MFA).
With MFA, in addition to a login and password, users provide something they possess, like a key, security token, or smartphone, to verify their identity. Thus, MFA minimizes the risks of unauthorized access to Active Directory.
Syteca offers two-factor authentication (2FA) that uses time-based one-time passcodes as a second authentication factor to help you protect your valuable assets. Syteca’s 2FA is also universal and cross-platform, so you can use it for both Linux and Windows servers.
4. Choose an appropriate access control model
Efficiently managing access controls is a surefire way to minimize security risks related to excessive access rights. There are two models that address this: role-based access control (RBAC) and attribute-based access control (ABAC).
Role-based access control
An access control method that assigns every employee a role. An employee can access objects and execute operations only if their role in the system has relevant permissions.
Attribute-based access control
An access control method in which attributes can be modified for the needs of a particular user without creating a new role.
Both access control models have their advantages and disadvantages, so choosing the right one depends on your organization’s characteristics and needs.
With the RBAC model, you can easily authorize, restrict, and revoke access for certain groups of users instead of dealing with each user independently. However, you can’t assign permissions to objects and operations, just as you can’t restrict access to certain data within a system.
The ABAC model provides you with the opportunity to describe a business rule of any complexity. For example, you can allow employees to access certain data only during work hours. On the downside, specifying and maintaining such complex policies makes an ABAC system challenging to configure and maintain.
5. Secure employees’ passwords
With 30% of all incidents resulting from the compromise and abuse of valid credentials, protecting password management in your organization must be among your top priorities.
The need to manage multiple credentials across systems and a lack of cybersecurity training can draw your employees into unsafe practices, such as storing passwords in browsers and sharing them via messengers. This can lead to data breaches as a result of the compromise of your Active Directory.
To protect your employees’ passwords, consider centralizing password management in your organization via specialized tools. Syteca’s workforce password management capabilities enable you to:
- Secure privileged credentials in an encrypted vault
- Provide secrets to users without exposing passwords
- Automate password rotation
- Establish secure password sharing between teams
- Grant one-time passwords to vendors
6. Manage shared accounts
Despite being unsafe, organizations tend to use shared accounts for network administration or working with third-party services. Thus, different users can log in to the same account under the same credentials to perform certain work-related activities.
But without proper management, shared accounts can become a source of cybersecurity threats, leaving you unable to identify the particular individual behind an incident.
Manage shared accounts

Review all accounts with shared access

Remove unnecessary permissions

Enable secondary authentication
First and foremost, review all shared accounts and check whether shared access is in fact required. If not, remove permissions for users who don’t need them. For the remaining shared accounts, it’s best to enable secondary authentication. This way, you’ll be able to distinguish the actions of particular users performed under a shared account and investigate any security incidents that occur.
You can also leverage Syteca’s capabilities as an endpoint access management solution, including secondary authentication to distinguish users of shared and built-in accounts. Gain full visibility into actions performed under generic credentials for root and admin accounts.
When selecting a PAM solution, pay attention to factors such as scalability, automation, and IT compliance coverage, in addition to functionality. You can learn how Syteca PAM addresses most of these factors in our article on how to choose a PAM solution.
Advanced monitoring and threat detection tips for AD security
Modern attackers can exploit legitimate credentials and processes to move undetected within your networks and Active Directory environments, making traditional detection methods insufficient.
By combining real-time AD monitoring, user activity recording, and automated incident response, you can identify and contain threats while maintaining full visibility into privileged user actions.
1
Monitor AD and system changes
2
Monitor privileged user activity
3
Automate threat response
1. Monitor AD and system changes
Continuous monitoring of key Active Directory components helps detect threats as they unfold. For example, abnormal Kerberos ticket activity or unauthorized changes to SYSVOL or registry settings can indicate malicious activity.
Consider monitoring the following:
- Authentication traffic
- DNS lookups and changes
- Registry modifications
Real-time visibility into these signals can help you detect malicious behavior faster and provide valuable forensic context for incident response teams.
2. Monitor privileged user activity
Privileged user monitoring is a common practice within organizations as it helps you understand what data users access and what changes they make. Thus, you can detect abnormalities in user behavior, which may indicate malicious activity or account compromise.
With Syteca UAM, you can easily establish robust monitoring of privileged user activity and leverage the following benefits:
- Monitor, record, and audit all privileged user sessions on selected endpoints
- Receive notifications about abnormal user actions
- Continue recording a session in offline mode if the server connection is lost
In addition, you can use Syteca to generate insightful user activity reports and analyze overall user activity within your organization.
3. Automate threat response
Manually monitoring audit logs can be time-consuming and inefficient. Automate the process of analyzing logs and generating alerts for critical events. This will allow your IT team to focus on investigating and responding to potential threats instead of spending time sifting through data.
Syteca UAM features a robust alerting system that streamlines threat detection and allows your security team to automate incident response as follows:
- Detect suspicious user activity in real-time
- Automatically terminate sessions and suspicious processes
- Notify users about policy violations
- View user sessions live upon detection of a potential threat
Secure your Active Directory with Syteca
Keeping your Active Directory environment protected against possible misuse and attacks is a significant part of an effective cybersecurity strategy. Implementing our tips for securing Active Directory — including the use of a powerful PAM solution as well as AD auditing and monitoring best practices — will ensure the security of your organization’s most critical assets.
With Syteca, you can effectively manage user access rights, monitor user sessions, and detect suspicious activity before it leads to a cybersecurity incident.
Want to try Syteca? Request access to the online demo!
See why clients from 70+ countries already use Syteca.